Chapter 19 ZipSlack
Table of Contents
19.1 What is ZipSlack?
19.2 Getting ZipSlack
19.3 Booting ZipSlack
19.1 What is ZipSlack?
ZipSlack is a special version of Slackware Linux. It's an already installed copy of Slackware that's ready to run from your DOS or Windows partition. It's a basic installation, you do not get everything that comes with Slackware.
ZipSlack gets its name from the form it's distributed in, a big .ZIP file. Users of DOS and Windows will probably be familiar with these files. They are compressed archives. The ZipSlack archive contains everything you need to get up and running with Slackware.
It is important to note that ZipSlack is significantly different from a regular installation. Even though they function the same and contain the same programs, their intended audiences and functions differ. Several advantages and disadvantages of ZipSlack are discussed below.
One last thing, you should always review the documentation included in the actual ZipSlack directory. It contains the latest information regarding installation, booting, and general use of the product.
19.1.1 Advantages
•Does not require repartitioning of your hard disk.
•Great way to learn Slackware Linux without stumbling through the installation process.
19.1.2 Disadvantages
•Uses the DOS filesystem, which is slower than a native Linux filesystem.
•Will not work with Windows NT.
http://www.slackbook.org/html/zipslack.html
Slackware Linux Essentials: Tutorial 18
Chapter 18 Slackware Package Management
Table of Contents
18.1 Overview of Package Format
18.2 Package Utilities
18.3 Making Packages
18.4 Making Tags and Tagfiles (for setup)
A software package is a bundle of related programs that are ready for you to install. When you download a source code archive, you have to configure, compile, and install it by hand. With a software package, this has already been done for you. All that you have to do is install the package. Another handy feature of using software packages is that it is very easy to remove and upgrade them, if you so desire. Slackware comes with programs for all your package management needs. You can install, remove, upgrade, make, and examine packages very easily.
There's a myth that's been going around ever since RedHat debuted RedHat Package Manager, that Slackware has no package management tool. This simply couldn't be further from the truth. Slackware has always included a package manager, even before RedHat existed. While not as full-featured or as ubiquitous as rpm (or for that matter deb), pkgtool and its associated programs are every bit as good at installing packages as rpm. The truth about pkgtool is not that it doesn't exist, but that it doesn't do any dependency checking.
Apparently many people in the Linux community think that a packager manager must by definition include dependency checking. Well, that simply isn't the case, as Slackware most certainly does not. This is not to say that Slackware packages don't have dependencies, but rather that its package manager doesn't check for them. Dependency management is left up to the sysadmin, and that's the way we like it.
18.1 Overview of Package Format
Before learning the utilities, you should become familiar with the format of a Slackware package. In Slackware, a package is simply a tar archive file that has been compressed with gzip. Packages are built to be extracted in the root directory.
Here is a fictitious program and its example package:
./
usr/
usr/bin/
usr/bin/makehejaz
usr/doc/
usr/doc/makehejaz-1.0/
usr/doc/makehejaz-1.0/COPYING
usr/doc/makehejaz-1.0/README
usr/man/
usr/man/man1
usr/man/man1/makehejaz.1.gz
install/
install/doinst.sh
The package system will extract this file in the root directory to install it. An entry in the package database will be created that contains the contents of this package so that it can be upgraded or removed later.
Notice the install/ subdirectory. This is a special directory that can contain a postinstallation script called doinst.sh. If the package system finds this file, it will execute it after installing the package.
Other scripts can be embedded in the package, but those are discussed more in detail in Section 18.3.2 below.
http://www.slackbook.org/html/package-management.html
Table of Contents
18.1 Overview of Package Format
18.2 Package Utilities
18.3 Making Packages
18.4 Making Tags and Tagfiles (for setup)
A software package is a bundle of related programs that are ready for you to install. When you download a source code archive, you have to configure, compile, and install it by hand. With a software package, this has already been done for you. All that you have to do is install the package. Another handy feature of using software packages is that it is very easy to remove and upgrade them, if you so desire. Slackware comes with programs for all your package management needs. You can install, remove, upgrade, make, and examine packages very easily.
There's a myth that's been going around ever since RedHat debuted RedHat Package Manager, that Slackware has no package management tool. This simply couldn't be further from the truth. Slackware has always included a package manager, even before RedHat existed. While not as full-featured or as ubiquitous as rpm (or for that matter deb), pkgtool and its associated programs are every bit as good at installing packages as rpm. The truth about pkgtool is not that it doesn't exist, but that it doesn't do any dependency checking.
Apparently many people in the Linux community think that a packager manager must by definition include dependency checking. Well, that simply isn't the case, as Slackware most certainly does not. This is not to say that Slackware packages don't have dependencies, but rather that its package manager doesn't check for them. Dependency management is left up to the sysadmin, and that's the way we like it.
18.1 Overview of Package Format
Before learning the utilities, you should become familiar with the format of a Slackware package. In Slackware, a package is simply a tar archive file that has been compressed with gzip. Packages are built to be extracted in the root directory.
Here is a fictitious program and its example package:
./
usr/
usr/bin/
usr/bin/makehejaz
usr/doc/
usr/doc/makehejaz-1.0/
usr/doc/makehejaz-1.0/COPYING
usr/doc/makehejaz-1.0/README
usr/man/
usr/man/man1
usr/man/man1/makehejaz.1.gz
install/
install/doinst.sh
The package system will extract this file in the root directory to install it. An entry in the package database will be created that contains the contents of this package so that it can be upgraded or removed later.
Notice the install/ subdirectory. This is a special directory that can contain a postinstallation script called doinst.sh. If the package system finds this file, it will execute it after installing the package.
Other scripts can be embedded in the package, but those are discussed more in detail in Section 18.3.2 below.
http://www.slackbook.org/html/package-management.html
Slackware Linux Essentials: Tutorial 17
Chapter 17 Emacs
Table of Contents
17.1 Starting emacs
17.2 Buffers
17.3 Modes
17.4 Basic Editing
17.5 Saving Files
While vi (with its clones) is without a doubt the most ubiquitous editor on Unix-like systems, Emacs comes in a good second. Instead of using different “modes”, like vi does, it uses Control and Alt key combinations to enter commands, in much the same way that you can use Control and Alt key combinations in a word processor and indeed in many other applications to execute certain functions. (Though it should be noted that the commands rarely correspond; so while many modern applications use Ctrl-C/ X/ V for copying, cutting and pasting, Emacs uses different keys and actually a somewhat different mechanism for this.)
Also unlike vi, which is an (excellent) editor and nothing more, Emacs is a program with near endless capabilities. Emacs is (for the most part) written in Lisp, which is a very powerful programming language that has the peculiar property that every program written in it is automatically a Lisp compiler of its own. This means that the user can extend Emacs, and in fact write completely new programs “in Emacs”.
As a result, Emacs is not just an editor anymore. There are many add-on packages for Emacs available (many come with the program's source) that provide all sorts of functionality. Many of these are related to text editing, which is after all Emacs' basic task, but it doesn't stop there. There are for example several spreadsheet programs for Emacs, there are databases, games, mail and news clients (the top one being Gnus), etc.
There are two main versions of Emacs: GNU Emacs (which is the version that comes with Slackware) and XEmacs. The latter is not a version for Emacs running under X. In fact, both Emacs and XEmacs run on the console as well as under X. XEmacs was once started as a project to tidy up the Emacs code. Currently, both versions are being actively developed, and there is in fact much interaction between the two development teams. For the present chapter, it is immaterial whether you use Emacs or XEmacs, the differences between them are not relevant to the normal user.
17.1 Starting emacs
Emacs can be started from the shell by simply typing emacs. When you are running X, Emacs will (normally) come up with its own X window, usually with a menu bar at the top, where you can find the most important functions. On startup, Emacs will first show a welcome message, and then after a few seconds will drop you in the *scratch* buffer. (See Section 17.2.)
You can also start Emacs on an existing file by typing
% emacs /etc/resolv.conf
This will cause Emacs to load the specified file when it starts up, skipping the welcome message.
17.1.1 Command Keys
As mentioned above, Emacs uses Control and Alt combinations for commands. The usual convention is to write these with C-letter and M-letter, respectively. So C-x means Control+x, and M-x means Alt+x. (The letter M is used instead of A because originally the key was not the Alt key but the Meta key. The Meta key has all but disappeared from computer keyboards, and in Emacs the Alt key has taken over its function.)
Many Emacs commands consist of sequences of keys and key combinations. For example, C-x C-c (that is Control-x followed by Control-c ) quits Emacs, C-x C-s saves the current file. Keep in mind that C-x C-b is not the same as C-x b. The former means Control-x followed by Control-b, while the latter means Control-x followed by just 'b'.
http://www.slackbook.org/html/emacs.html
Table of Contents
17.1 Starting emacs
17.2 Buffers
17.3 Modes
17.4 Basic Editing
17.5 Saving Files
While vi (with its clones) is without a doubt the most ubiquitous editor on Unix-like systems, Emacs comes in a good second. Instead of using different “modes”, like vi does, it uses Control and Alt key combinations to enter commands, in much the same way that you can use Control and Alt key combinations in a word processor and indeed in many other applications to execute certain functions. (Though it should be noted that the commands rarely correspond; so while many modern applications use Ctrl-C/ X/ V for copying, cutting and pasting, Emacs uses different keys and actually a somewhat different mechanism for this.)
Also unlike vi, which is an (excellent) editor and nothing more, Emacs is a program with near endless capabilities. Emacs is (for the most part) written in Lisp, which is a very powerful programming language that has the peculiar property that every program written in it is automatically a Lisp compiler of its own. This means that the user can extend Emacs, and in fact write completely new programs “in Emacs”.
As a result, Emacs is not just an editor anymore. There are many add-on packages for Emacs available (many come with the program's source) that provide all sorts of functionality. Many of these are related to text editing, which is after all Emacs' basic task, but it doesn't stop there. There are for example several spreadsheet programs for Emacs, there are databases, games, mail and news clients (the top one being Gnus), etc.
There are two main versions of Emacs: GNU Emacs (which is the version that comes with Slackware) and XEmacs. The latter is not a version for Emacs running under X. In fact, both Emacs and XEmacs run on the console as well as under X. XEmacs was once started as a project to tidy up the Emacs code. Currently, both versions are being actively developed, and there is in fact much interaction between the two development teams. For the present chapter, it is immaterial whether you use Emacs or XEmacs, the differences between them are not relevant to the normal user.
17.1 Starting emacs
Emacs can be started from the shell by simply typing emacs. When you are running X, Emacs will (normally) come up with its own X window, usually with a menu bar at the top, where you can find the most important functions. On startup, Emacs will first show a welcome message, and then after a few seconds will drop you in the *scratch* buffer. (See Section 17.2.)
You can also start Emacs on an existing file by typing
% emacs /etc/resolv.conf
This will cause Emacs to load the specified file when it starts up, skipping the welcome message.
17.1.1 Command Keys
As mentioned above, Emacs uses Control and Alt combinations for commands. The usual convention is to write these with C-letter and M-letter, respectively. So C-x means Control+x, and M-x means Alt+x. (The letter M is used instead of A because originally the key was not the Alt key but the Meta key. The Meta key has all but disappeared from computer keyboards, and in Emacs the Alt key has taken over its function.)
Many Emacs commands consist of sequences of keys and key combinations. For example, C-x C-c (that is Control-x followed by Control-c ) quits Emacs, C-x C-s saves the current file. Keep in mind that C-x C-b is not the same as C-x b. The former means Control-x followed by Control-b, while the latter means Control-x followed by just 'b'.
http://www.slackbook.org/html/emacs.html
Slackware Linux Essentials: Tutorial 16
Chapter 16 Vi
Table of Contents
16.1 Starting vi
16.2 Modes
16.3 Opening Files
16.4 Saving Files
16.5 Quitting vi
16.6 vi Configuration
16.7 Vi Keys
vi(1) is the standard Unix text editing program, and while mastering it is not as essential as it once was, is still a very rewarding goal. There are several versions (or clones) of vi available, including vi, elvis, vile, and vim. One of these is available on just about any version of Unix, as well as on Linux. All of these versions include the same basic feature set and commands, so learning one clone should make it easy to learn another. With the variety of text editors included with Linux distributions and Unix variants these days, many people no longer use vi. Still, it remains the most universal text editor across Unix and Unix work-alikes. Mastering vi means you should never be sitting at a Unix machine and not be comfortable with at least one powerful text editor.
vi includes a number of powerful features including syntax highlighting, code formatting, a powerful search-and-replace mechanism, macros, and more. These features make it especially attractive to programmers, web developers, and the like. System administrators will appreciate the automation and integration with the shell that is possible.
On Slackware Linux, the default version of vi available is elvis. Other versions - including vim and gvim - are available if you've installed the proper packages. gvim is an X Window version of vim that includes toolbars, detachable menus, and dialog boxes.
16.1 Starting vi
vi can be started from the command line in a variety of ways. The simplest form is just:
% vi
Figure 16-1. A vi session.
This will start up vi with an empty buffer. At this point, you'll see a mostly blank screen. It is now in “command mode”, waiting for you to do something. For a discussion of the various vi modes, see the Section 16.2. In order to quit out of vi, type the following:
:q
Assuming that there have been no changes to the file, this will cause vi to quit. If there have been changes made, it will warn you that there have been changes and tell you how to disregard them. Disregarding changes usually means appending an exclamation point after the “q” like so:
:q!
The exclamation point usually means to force some action. We'll discuss it and other key combinations in further details later.
You can also start vi with a pre-existing file. For example, the file /etc/resolv.conf would be opened like so:
% vi /etc/resolv.conf
Finally, vi can be started on a particular line of a file. This is especially useful for programmers when an error message includes the line their program bombed on. For example, you could start up vi on line 47 of /usr/src/linux/init/main.c like so:
% vi +47 /usr/src/linux/init/main.c
vi will display the given file and will place the cursor at the specified line. In the case where you specify a line that is after the end of the file, vi will place the cursor on the last line. This is especially helpful for programmers, as they can jump straight to the location in the file that an error occurred, without having to search for it.
http://www.slackbook.org/html/vi.html
Table of Contents
16.1 Starting vi
16.2 Modes
16.3 Opening Files
16.4 Saving Files
16.5 Quitting vi
16.6 vi Configuration
16.7 Vi Keys
vi(1) is the standard Unix text editing program, and while mastering it is not as essential as it once was, is still a very rewarding goal. There are several versions (or clones) of vi available, including vi, elvis, vile, and vim. One of these is available on just about any version of Unix, as well as on Linux. All of these versions include the same basic feature set and commands, so learning one clone should make it easy to learn another. With the variety of text editors included with Linux distributions and Unix variants these days, many people no longer use vi. Still, it remains the most universal text editor across Unix and Unix work-alikes. Mastering vi means you should never be sitting at a Unix machine and not be comfortable with at least one powerful text editor.
vi includes a number of powerful features including syntax highlighting, code formatting, a powerful search-and-replace mechanism, macros, and more. These features make it especially attractive to programmers, web developers, and the like. System administrators will appreciate the automation and integration with the shell that is possible.
On Slackware Linux, the default version of vi available is elvis. Other versions - including vim and gvim - are available if you've installed the proper packages. gvim is an X Window version of vim that includes toolbars, detachable menus, and dialog boxes.
16.1 Starting vi
vi can be started from the command line in a variety of ways. The simplest form is just:
% vi
Figure 16-1. A vi session.
This will start up vi with an empty buffer. At this point, you'll see a mostly blank screen. It is now in “command mode”, waiting for you to do something. For a discussion of the various vi modes, see the Section 16.2. In order to quit out of vi, type the following:
:q
Assuming that there have been no changes to the file, this will cause vi to quit. If there have been changes made, it will warn you that there have been changes and tell you how to disregard them. Disregarding changes usually means appending an exclamation point after the “q” like so:
:q!
The exclamation point usually means to force some action. We'll discuss it and other key combinations in further details later.
You can also start vi with a pre-existing file. For example, the file /etc/resolv.conf would be opened like so:
% vi /etc/resolv.conf
Finally, vi can be started on a particular line of a file. This is especially useful for programmers when an error message includes the line their program bombed on. For example, you could start up vi on line 47 of /usr/src/linux/init/main.c like so:
% vi +47 /usr/src/linux/init/main.c
vi will display the given file and will place the cursor at the specified line. In the case where you specify a line that is after the end of the file, vi will place the cursor on the last line. This is especially helpful for programmers, as they can jump straight to the location in the file that an error occurred, without having to search for it.
http://www.slackbook.org/html/vi.html
Slackware Linux Essentials: Tutorial 15
Chapter 15 Archive Files
Table of Contents
15.1 gzip
15.2 bzip2
15.3 tar
15.4 zip
15.1 gzip
gzip(1) is the GNU compression program. It takes a single file and compresses it. The basic usage is as follows:
% gzip filename
The resulting file will be named filename.gz and will usually be smaller than the input file. Note that filename.gz will replace filename. This means that filename will no longer exist, even though a gzipped copy will. Regular text files will compress nicely, while jpeg images, mp3s, and other such files will not compress too well as they are already compressed. This basic usage is a balance of final file size and compression time. The maximum compression can be achieved like so:
% gzip -9 filename
This will take a longer time to compress the file, but the result will be as small as gzip can make it. Using lower values for the command line option will cause it to compress faster, but the file will not be as compressed.
Decompressing gzipped files can be done using two commands, which are really just the same program. gzip will decompress any file with a recognized file extension. A recognized extension can be any of the following: .gz, -gz, .z, -z, .Z, or -Z. The first method is to call gunzip(1) on a file, like so:
% gunzip filename.gz
This will leave a decompressed version of infile in the current directory, and the .gz extension will be stripped from the filename. gunzip is really part of gzip and is identical to gzip -d. As such, gzip is often pronounced gunzip, as that name just sounds cooler. :^)
http://www.slackbook.org/html/archive-files.html
Table of Contents
15.1 gzip
15.2 bzip2
15.3 tar
15.4 zip
15.1 gzip
gzip(1) is the GNU compression program. It takes a single file and compresses it. The basic usage is as follows:
% gzip filename
The resulting file will be named filename.gz and will usually be smaller than the input file. Note that filename.gz will replace filename. This means that filename will no longer exist, even though a gzipped copy will. Regular text files will compress nicely, while jpeg images, mp3s, and other such files will not compress too well as they are already compressed. This basic usage is a balance of final file size and compression time. The maximum compression can be achieved like so:
% gzip -9 filename
This will take a longer time to compress the file, but the result will be as small as gzip can make it. Using lower values for the command line option will cause it to compress faster, but the file will not be as compressed.
Decompressing gzipped files can be done using two commands, which are really just the same program. gzip will decompress any file with a recognized file extension. A recognized extension can be any of the following: .gz, -gz, .z, -z, .Z, or -Z. The first method is to call gunzip(1) on a file, like so:
% gunzip filename.gz
This will leave a decompressed version of infile in the current directory, and the .gz extension will be stripped from the filename. gunzip is really part of gzip and is identical to gzip -d. As such, gzip is often pronounced gunzip, as that name just sounds cooler. :^)
http://www.slackbook.org/html/archive-files.html
Slackware Linux Essentials: Tutorial 14
Chapter 14 Security
Table of Contents
14.1 Disabling Services
14.2 Host Access Control
14.3 Keeping Current
Security on any system is important; it can prevent people launching attacks from your machine, as well as protect sensitive data. This chapter is all about how to start securing your Slackware box against script kiddies, crackers and rogue hamsters alike. Bear in mind that this is only the start of securing a system; security is a process, not a state.
14.1 Disabling Services
The first step after installing Slackware should be to disable any services you don't need. Any services could potentially pose a security risk, so it is important to run as few services as possible (i.e. only those that are needed). Services are started from two main places - inetd and init scripts.
14.1.1 Services started from inetd
A lot of the daemons that come with Slackware are run from inetd(8). inetd is a daemon that listens on all of the ports used by services configured to be started by it and spawns an instance of the relevant daemon when a connection attempt is made. Daemons started from inetd can be disabled by commenting out the relevant lines in /etc/inetd.conf. To do this, open this file in your favorite editor (e.g. vi) and you should see lines similar to this:
telnet stream tcp nowait root /usr/sbin/tcpd in.telnetd
You can disable this service, and any others you don't need, by commenting them out (i.e. adding a # (hash) symbol to the beginning of the line). The above line would then become:
#telnet stream tcp nowait root /usr/sbin/tcpd in.telnetd
After inetd has been restarted, this service will be disabled. You can restart inetd with the command:
# kill -HUP $(cat /var/run/inetd.pid)
14.1.2 Services started from init scripts
The rest of the services started when the machine starts are started from the init scripts in /etc/rc.d/. These can be disabled in two different ways, the first being to remove the execute permissions on the relevant init script and the second being to comment out the relevant lines in the init scripts.
For example, SSH is started by its own init script at /etc/rc.d/rc.sshd. You can disable this using:
# chmod -x /etc/rc.d/rc.sshd
For services that don't have their own init script, you will need to comment out the relevant lines in the init scripts to disable them. For example, the portmap daemon is started by the following lines in /etc/rc.d/rc.inet2:
# This must be running in order to mount NFS volumes.
# Start the RPC portmapper:
if [ -x /sbin/rpc.portmap ]; then
echo "Starting RPC portmapper: /sbin/rpc.portmap"
/sbin/rpc.portmap
fi
# Done starting the RPC portmapper.
This can be disabled by adding # symbols to the beginnings of the lines that don't already start with them, like so:
# This must be running in order to mount NFS volumes.
# Start the RPC portmapper:
#if [ -x /sbin/rpc.portmap ]; then
# echo "Starting RPC portmapper: /sbin/rpc.portmap"
# /sbin/rpc.portmap
#fi
# Done starting the RPC portmapper.
These changes will only take effect after either a reboot or changing from and back to runlevel 3 or 4. You can do this by typing the following on the console (you will need to log in again after changing to runlevel 1):
# telinit 1
# telinit 3
http://www.slackbook.org/html/security.html
Table of Contents
14.1 Disabling Services
14.2 Host Access Control
14.3 Keeping Current
Security on any system is important; it can prevent people launching attacks from your machine, as well as protect sensitive data. This chapter is all about how to start securing your Slackware box against script kiddies, crackers and rogue hamsters alike. Bear in mind that this is only the start of securing a system; security is a process, not a state.
14.1 Disabling Services
The first step after installing Slackware should be to disable any services you don't need. Any services could potentially pose a security risk, so it is important to run as few services as possible (i.e. only those that are needed). Services are started from two main places - inetd and init scripts.
14.1.1 Services started from inetd
A lot of the daemons that come with Slackware are run from inetd(8). inetd is a daemon that listens on all of the ports used by services configured to be started by it and spawns an instance of the relevant daemon when a connection attempt is made. Daemons started from inetd can be disabled by commenting out the relevant lines in /etc/inetd.conf. To do this, open this file in your favorite editor (e.g. vi) and you should see lines similar to this:
telnet stream tcp nowait root /usr/sbin/tcpd in.telnetd
You can disable this service, and any others you don't need, by commenting them out (i.e. adding a # (hash) symbol to the beginning of the line). The above line would then become:
#telnet stream tcp nowait root /usr/sbin/tcpd in.telnetd
After inetd has been restarted, this service will be disabled. You can restart inetd with the command:
# kill -HUP $(cat /var/run/inetd.pid)
14.1.2 Services started from init scripts
The rest of the services started when the machine starts are started from the init scripts in /etc/rc.d/. These can be disabled in two different ways, the first being to remove the execute permissions on the relevant init script and the second being to comment out the relevant lines in the init scripts.
For example, SSH is started by its own init script at /etc/rc.d/rc.sshd. You can disable this using:
# chmod -x /etc/rc.d/rc.sshd
For services that don't have their own init script, you will need to comment out the relevant lines in the init scripts to disable them. For example, the portmap daemon is started by the following lines in /etc/rc.d/rc.inet2:
# This must be running in order to mount NFS volumes.
# Start the RPC portmapper:
if [ -x /sbin/rpc.portmap ]; then
echo "Starting RPC portmapper: /sbin/rpc.portmap"
/sbin/rpc.portmap
fi
# Done starting the RPC portmapper.
This can be disabled by adding # symbols to the beginnings of the lines that don't already start with them, like so:
# This must be running in order to mount NFS volumes.
# Start the RPC portmapper:
#if [ -x /sbin/rpc.portmap ]; then
# echo "Starting RPC portmapper: /sbin/rpc.portmap"
# /sbin/rpc.portmap
#fi
# Done starting the RPC portmapper.
These changes will only take effect after either a reboot or changing from and back to runlevel 3 or 4. You can do this by typing the following on the console (you will need to log in again after changing to runlevel 1):
# telinit 1
# telinit 3
http://www.slackbook.org/html/security.html
Slackware Linux Essentials: Tutorial 13
Chapter 13 Basic Network Commands
Table of Contents
13.1 ping
13.2 traceroute
13.3 DNS Tools
13.4 finger
13.5 telnet
13.6 The Secure shell
13.7 email
13.8 Browsers
13.9 FTP Clients
13.10 Talking to Other People
A network consists of several computers connected together. The network can be as simple as a few computers connected in your home or office, or as complicated as a large university network or even the entire Internet. When your computer is part of a network, you have access to those systems either directly or through services like mail and the web.
There are a variety of networking programs that you can use. Some are handy for performing diagnostics to see if everything is working properly. Others (like mail readers and web browsers) are useful for getting your work done and staying in contact with other people.
13.1 ping
ping(8) sends an ICMP ECHO_REQUEST packet to the specified host. If the host responds, you get an ICMP packet back. Sound strange? Well, you can “ping” an IP address to see if a machine is alive. If there is no response, you know something is wrong. Here is an example conversation between two Linux users:
User A: Loki's down again.
User B: Are you sure?
User A: Yeah, I tried pinging it, but there's no response.
It's instances like these that make ping a very useful day-to-day command. It provides a very quick way to see if a machine is up and connected to the network. The basic syntax is:
% ping www.slackware.com
There are, of course, several options that can be specified. Check the ping(1) man page for more information.
http://www.slackbook.org/html/basic-network-commands.html
Table of Contents
13.1 ping
13.2 traceroute
13.3 DNS Tools
13.4 finger
13.5 telnet
13.6 The Secure shell
13.7 email
13.8 Browsers
13.9 FTP Clients
13.10 Talking to Other People
A network consists of several computers connected together. The network can be as simple as a few computers connected in your home or office, or as complicated as a large university network or even the entire Internet. When your computer is part of a network, you have access to those systems either directly or through services like mail and the web.
There are a variety of networking programs that you can use. Some are handy for performing diagnostics to see if everything is working properly. Others (like mail readers and web browsers) are useful for getting your work done and staying in contact with other people.
13.1 ping
ping(8) sends an ICMP ECHO_REQUEST packet to the specified host. If the host responds, you get an ICMP packet back. Sound strange? Well, you can “ping” an IP address to see if a machine is alive. If there is no response, you know something is wrong. Here is an example conversation between two Linux users:
User A: Loki's down again.
User B: Are you sure?
User A: Yeah, I tried pinging it, but there's no response.
It's instances like these that make ping a very useful day-to-day command. It provides a very quick way to see if a machine is up and connected to the network. The basic syntax is:
% ping www.slackware.com
There are, of course, several options that can be specified. Check the ping(1) man page for more information.
http://www.slackbook.org/html/basic-network-commands.html
Slackware Linux Essentials: Tutorial 12
Chapter 12 Essential System Administration
Table of Contents
12.1 Users and Groups
12.2 Users and Groups, the Hard Way
12.3 Shutting Down Properly
Whoa whoa whoa whoa whoa.... I know what you're thinking. “I'm not a system administrator! I don't even want to be a system administrator!”
Fact is, you are the administrator of any computers for which you have the root password. This might be your desktop box with one or two users, or it might be a big server with several hundred. Regardless, you'll need to know how to manage users, and how to shut down the system safely. These tasks seem simple, but they have some quirks to keep in mind.
12.1 Users and Groups
As mentioned in Chapter 8, you shouldn't normally use your system logged in as root. Instead, you should create a normal user account for everyday use, and use the root account only for system administration tasks. To create a user, you can either use the tools supplied with Slackware, or you can edit the password files by hand.
12.1.1 Supplied Scripts
The easiest way to manage users and groups is with the supplied scripts and programs. Slackware includes the programs adduser, userdel(8), chfn(1), chsh(1), and passwd(1) for dealing with users. The commands groupadd(8), groupdel(8), and groupmod(8) are for dealing with groups. With the exception of chfn, chsh, and passwd, these programs are generally only run as root, and are therefore located in /usr/sbin. chfn, chsh, and passwd can be run by anyone, and are located in /usr/bin.
Users can be added with the adduser program. We'll start out by going through the whole procedure, showing all the questions that are asked and a brief description of what everything means. The default answer is in the brackets, and can be chosen for almost all the questions, unless you really want to change something.
# adduser
Login name for new user []: jellyd
This is the name that the user will use to login. Traditionally, login names are eight characters or fewer, and all lowercase characters. (You may use more than eight characters, or use digits, but avoid doing so unless you have a fairly important reason.)
You can also provide the login name as an argument on the command line:
# adduser jellyd
In either case, after providing the login name, adduser will prompt for the user ID:
User ID ('UID') [ defaults to next available ]:
The user ID (UID) is how ownerships are really determined in Linux. Each user has a unique number, starting at 1000 in Slackware. You can pick a UID for the new user, or you can just let adduser assign the user the next free one.
Initial group [users]:
All users are placed into the users group by default. You might want to place the new user into a different group, but it is not recommended unless you know what you're doing.
Additional groups (comma separated) []:
This question allows you to place the new user into additional groups. It is possible for a user to be in several groups at the same time. This is useful if you have established groups for things like modifying web site files, playing games, and so on. For example, some sites define group wheel as the only group that can use the su command. Or, a default Slackware installation uses the sys group for users authorized to play sounds through the internal sound card.
Home directory [/home/jellyd]
Home directories default to being placed under /home. If you run a very large system, it's possible that you have moved the home directories to a different location (or to many locations). This step allows you to specify where the user's home directory will be.
Shell [ /bin/bash ]
bash is the default shell for Slackware Linux, and will be fine for most people. If your new user comes from a Unix background, they may be familiar with a different shell. You can change their shell now, or they can change it themselves later using the chsh command.
Expiry date (YYYY-MM-DD) []:
Accounts can be set up to expire on a specified date. By default, there is no expiration date. You can change that, if you'd like. This option might be useful for people running an ISP who might want to make an account expire upon a certain date, unless they receive the next year's payment.
New account will be created as follows:
---------------------------------------
Login name: jellyd
UID: [ Next available ]
Initial group: users
Additional groups: [ None ]
Home directory: /home/jellyd
Shell: /bin/bash
Expiry date: [ Never ]
This is it... if you want to bail out, hit Control+C. Otherwise, press ENTER to go ahead and make the account.
You now see all the information that you've entered about the new account and are given the opportunity to abort the account creation. If you entered something incorrectly, you should hit Control+C and start over. Otherwise, you can hit enter and the account will be made.
Creating new account...
Changing the user information for jellyd
Enter the new value, or press return for the default
Full Name []: Jeremy
Room Number []: Smith 130
Work Phone []:
Home Phone []:
Other []:
All of this information is optional. You don't have to enter any of this if you don't want to, and the user can change it at any time using chfn. However, you might find it helpful to enter at least the full name and a phone number, in case you need to get in touch with the person later.
Changing password for jellyd
Enter the new password (minimum of 5, maximum of 127 characters)
Please use a combination of upper and lower case letters and numbers.
New password:
Re-enter new password:
Password changed.
Account setup complete.
You'll have to enter a password for the new user. Generally, if the new user is not physically present at this point, you'll just pick some default password and tell the user to change it to something more secure.
Choosing a Password: Having a secure password is the first line of defense against getting cracked. You do not want to have an easily guessed password, because that makes it easier for someone to break into your system. Ideally, a secure password would be a random string of characters, including upper and lowercase letters, numbers, and random characters. (A tab character might not be a wise choice, depending on what kinds of computers you'll be logging in from.) There are many software packages that can generate random passwords for you; search the Internet for these utilities.
In general, just use common sense: don't pick a password that is someone's birthday, a common phrase, something found on your desk, or anything that is easily associated with you. A password like “secure1” or any other password you see in print or online is also bad.
Removing users is not difficult at all. Just run userdel with the name of the account to remove. You should verify that the user is not logged in, and that no processes are running as that user. Also, remember that once you've deleted the user, all of that user's password information is gone permanently.
# userdel jellyd
This command removes that annoying jellyd user from your system. Good riddance! :) The user is removed from the /etc/passwd, /etc/shadow, and /etc/group files, but doesn't remove the user's home directory.
If you'd wanted to remove the home directory as well, you would instead use this command:
# userdel -r jellyd
Temporarily disabling an account will be covered in the next section on passwords, since a temporary change involves changing the user's password. Changing other account information is covered in Section 12.1.3.
The programs to add and remove groups are very simple. groupadd will just add another entry to the /etc/group file with a unique group ID, while groupdel will remove the specified group. It is up to you to edit /etc/group to add users to a specific group. For example, to add a group called cvs:
# groupadd cvs
And to remove it:
# groupdel cvs
12.1.2 Changing Passwords
The passwd program changes passwords by modifying the /etc/shadow file. This file holds all the passwords for the system in an encrypted format. In order to change your own password, you would type:
% passwd
Changing password for chris
Old password:
Enter the new password (minumum of 5, maximum of 127 characters)
Please use a combination of upper and lower case letters and numbers.
New password:
As you can see, you are prompted to enter your old password. It won't appear on the screen as you type it, just like when you log in. Then, you are prompted to enter the new password. passwd performs a lot of checks on your new password, and it will complain if your new password doesn't pass its checks. You can ignore its warnings if you want. You will be prompted to enter your new password a second time for confirmation.
If you are root, you can also change another user's password:
# passwd ted
You will then have to go through the same procedure as above, except that you won't have to enter the user's old password. (One of the many benefits of being root...)
If needed, you can also temporarily disable an account, and reenable it at a later time if needed. Both disabling an account and reenabling an account can be done with passwd. To disable an account, do the following as root:
# passwd -l david
This will change david's password to something that can never match any encrypted value. You would reenable the account by using:
# passwd -u david
Now, david's account is back to normal. Disabling an account might be useful if the user doesn't play by the rules you've set up on your system, or if they've exported a very large copy of xeyes(1) to your X desktop.
12.1.3 Changing User Information
There are two pieces of information that users can change at any time: their shell and their finger information. Slackware Linux uses chsh (change shell) and chfn (change finger) to modify these values.
A user can pick any shell that is listed in the /etc/shells file. For most people, /bin/bash will do just fine. Others might be familiar with a shell found on their system at work or school and want to use what they already know. To change your shell, use chsh:
% chsh
Password:
Changing the login shell for chris
Enter the new value, or press return for the default
Login Shell [/bin/bash]:
After entering your password, enter the full path to the new shell. Make sure that it's listed in the /etc/shells(5) file first. The root user can also change any user's shell by running chsh with a username as the argument.
The finger information is the optional information such as your full name, phone numbers, and room number. This can be changed using chfn, and follows the same procedure as it did during account creation. As usual, root can change anyone's finger information.
http://www.slackbook.org/html/essential-sysadmin.html
Table of Contents
12.1 Users and Groups
12.2 Users and Groups, the Hard Way
12.3 Shutting Down Properly
Whoa whoa whoa whoa whoa.... I know what you're thinking. “I'm not a system administrator! I don't even want to be a system administrator!”
Fact is, you are the administrator of any computers for which you have the root password. This might be your desktop box with one or two users, or it might be a big server with several hundred. Regardless, you'll need to know how to manage users, and how to shut down the system safely. These tasks seem simple, but they have some quirks to keep in mind.
12.1 Users and Groups
As mentioned in Chapter 8, you shouldn't normally use your system logged in as root. Instead, you should create a normal user account for everyday use, and use the root account only for system administration tasks. To create a user, you can either use the tools supplied with Slackware, or you can edit the password files by hand.
12.1.1 Supplied Scripts
The easiest way to manage users and groups is with the supplied scripts and programs. Slackware includes the programs adduser, userdel(8), chfn(1), chsh(1), and passwd(1) for dealing with users. The commands groupadd(8), groupdel(8), and groupmod(8) are for dealing with groups. With the exception of chfn, chsh, and passwd, these programs are generally only run as root, and are therefore located in /usr/sbin. chfn, chsh, and passwd can be run by anyone, and are located in /usr/bin.
Users can be added with the adduser program. We'll start out by going through the whole procedure, showing all the questions that are asked and a brief description of what everything means. The default answer is in the brackets, and can be chosen for almost all the questions, unless you really want to change something.
# adduser
Login name for new user []: jellyd
This is the name that the user will use to login. Traditionally, login names are eight characters or fewer, and all lowercase characters. (You may use more than eight characters, or use digits, but avoid doing so unless you have a fairly important reason.)
You can also provide the login name as an argument on the command line:
# adduser jellyd
In either case, after providing the login name, adduser will prompt for the user ID:
User ID ('UID') [ defaults to next available ]:
The user ID (UID) is how ownerships are really determined in Linux. Each user has a unique number, starting at 1000 in Slackware. You can pick a UID for the new user, or you can just let adduser assign the user the next free one.
Initial group [users]:
All users are placed into the users group by default. You might want to place the new user into a different group, but it is not recommended unless you know what you're doing.
Additional groups (comma separated) []:
This question allows you to place the new user into additional groups. It is possible for a user to be in several groups at the same time. This is useful if you have established groups for things like modifying web site files, playing games, and so on. For example, some sites define group wheel as the only group that can use the su command. Or, a default Slackware installation uses the sys group for users authorized to play sounds through the internal sound card.
Home directory [/home/jellyd]
Home directories default to being placed under /home. If you run a very large system, it's possible that you have moved the home directories to a different location (or to many locations). This step allows you to specify where the user's home directory will be.
Shell [ /bin/bash ]
bash is the default shell for Slackware Linux, and will be fine for most people. If your new user comes from a Unix background, they may be familiar with a different shell. You can change their shell now, or they can change it themselves later using the chsh command.
Expiry date (YYYY-MM-DD) []:
Accounts can be set up to expire on a specified date. By default, there is no expiration date. You can change that, if you'd like. This option might be useful for people running an ISP who might want to make an account expire upon a certain date, unless they receive the next year's payment.
New account will be created as follows:
---------------------------------------
Login name: jellyd
UID: [ Next available ]
Initial group: users
Additional groups: [ None ]
Home directory: /home/jellyd
Shell: /bin/bash
Expiry date: [ Never ]
This is it... if you want to bail out, hit Control+C. Otherwise, press ENTER to go ahead and make the account.
You now see all the information that you've entered about the new account and are given the opportunity to abort the account creation. If you entered something incorrectly, you should hit Control+C and start over. Otherwise, you can hit enter and the account will be made.
Creating new account...
Changing the user information for jellyd
Enter the new value, or press return for the default
Full Name []: Jeremy
Room Number []: Smith 130
Work Phone []:
Home Phone []:
Other []:
All of this information is optional. You don't have to enter any of this if you don't want to, and the user can change it at any time using chfn. However, you might find it helpful to enter at least the full name and a phone number, in case you need to get in touch with the person later.
Changing password for jellyd
Enter the new password (minimum of 5, maximum of 127 characters)
Please use a combination of upper and lower case letters and numbers.
New password:
Re-enter new password:
Password changed.
Account setup complete.
You'll have to enter a password for the new user. Generally, if the new user is not physically present at this point, you'll just pick some default password and tell the user to change it to something more secure.
Choosing a Password: Having a secure password is the first line of defense against getting cracked. You do not want to have an easily guessed password, because that makes it easier for someone to break into your system. Ideally, a secure password would be a random string of characters, including upper and lowercase letters, numbers, and random characters. (A tab character might not be a wise choice, depending on what kinds of computers you'll be logging in from.) There are many software packages that can generate random passwords for you; search the Internet for these utilities.
In general, just use common sense: don't pick a password that is someone's birthday, a common phrase, something found on your desk, or anything that is easily associated with you. A password like “secure1” or any other password you see in print or online is also bad.
Removing users is not difficult at all. Just run userdel with the name of the account to remove. You should verify that the user is not logged in, and that no processes are running as that user. Also, remember that once you've deleted the user, all of that user's password information is gone permanently.
# userdel jellyd
This command removes that annoying jellyd user from your system. Good riddance! :) The user is removed from the /etc/passwd, /etc/shadow, and /etc/group files, but doesn't remove the user's home directory.
If you'd wanted to remove the home directory as well, you would instead use this command:
# userdel -r jellyd
Temporarily disabling an account will be covered in the next section on passwords, since a temporary change involves changing the user's password. Changing other account information is covered in Section 12.1.3.
The programs to add and remove groups are very simple. groupadd will just add another entry to the /etc/group file with a unique group ID, while groupdel will remove the specified group. It is up to you to edit /etc/group to add users to a specific group. For example, to add a group called cvs:
# groupadd cvs
And to remove it:
# groupdel cvs
12.1.2 Changing Passwords
The passwd program changes passwords by modifying the /etc/shadow file. This file holds all the passwords for the system in an encrypted format. In order to change your own password, you would type:
% passwd
Changing password for chris
Old password:
Enter the new password (minumum of 5, maximum of 127 characters)
Please use a combination of upper and lower case letters and numbers.
New password:
As you can see, you are prompted to enter your old password. It won't appear on the screen as you type it, just like when you log in. Then, you are prompted to enter the new password. passwd performs a lot of checks on your new password, and it will complain if your new password doesn't pass its checks. You can ignore its warnings if you want. You will be prompted to enter your new password a second time for confirmation.
If you are root, you can also change another user's password:
# passwd ted
You will then have to go through the same procedure as above, except that you won't have to enter the user's old password. (One of the many benefits of being root...)
If needed, you can also temporarily disable an account, and reenable it at a later time if needed. Both disabling an account and reenabling an account can be done with passwd. To disable an account, do the following as root:
# passwd -l david
This will change david's password to something that can never match any encrypted value. You would reenable the account by using:
# passwd -u david
Now, david's account is back to normal. Disabling an account might be useful if the user doesn't play by the rules you've set up on your system, or if they've exported a very large copy of xeyes(1) to your X desktop.
12.1.3 Changing User Information
There are two pieces of information that users can change at any time: their shell and their finger information. Slackware Linux uses chsh (change shell) and chfn (change finger) to modify these values.
A user can pick any shell that is listed in the /etc/shells file. For most people, /bin/bash will do just fine. Others might be familiar with a shell found on their system at work or school and want to use what they already know. To change your shell, use chsh:
% chsh
Password:
Changing the login shell for chris
Enter the new value, or press return for the default
Login Shell [/bin/bash]:
After entering your password, enter the full path to the new shell. Make sure that it's listed in the /etc/shells(5) file first. The root user can also change any user's shell by running chsh with a username as the argument.
The finger information is the optional information such as your full name, phone numbers, and room number. This can be changed using chfn, and follows the same procedure as it did during account creation. As usual, root can change anyone's finger information.
http://www.slackbook.org/html/essential-sysadmin.html
Slackware Linux Essentials: Tutorial 11
Chapter 11 Process Control
Table of Contents
11.1 Backgrounding
11.2 Foregrounding
11.3 ps
11.4 kill
11.5 top
Every program that is running is called a process. These processes range from things like the X Window System to system programs (daemons) that are started when the computer boots. Every process runs as a particular user. Processes that are started at boot time usually run as root or nobody. Processes that you start will run as you. Processes started as other users will run as those users.
You have control over all the processes that you start. Additionally, root has control over all processes on the system, including those started by other users. Processes can be controlled and monitored through several programs, as well as some shell commands.
11.1 Backgrounding
Programs started from the command line start up in the foreground. This allows you to see all the output of the program and interact with it. However, there are several occasions when you'd like the program to run without taking up your terminal. This is called running the program in the background, and there are a few ways to do it.
The first way to background a process is by adding an ampersand to the command line when you start the program. For example, assume you wanted to use the command line mp3 player amp to play a directory full of mp3s, but you needed to do something else on the same terminal. The following command line would start up amp in the background:
% amp *.mp3 &
The program will run as normal, and you are returned to a prompt.
The other way to background a process is to do so while it is running. First, start up a program. While it is running, hit Control+z. This suspends the process. A suspended process is basically paused. It momentarily stops running, but can be started up again at any time. Once you have suspended a process, you are returned to a prompt. You can background the process by typing:
% bg
Now the suspended process is running in the background.
http://www.slackbook.org/html/process-control.html
Table of Contents
11.1 Backgrounding
11.2 Foregrounding
11.3 ps
11.4 kill
11.5 top
Every program that is running is called a process. These processes range from things like the X Window System to system programs (daemons) that are started when the computer boots. Every process runs as a particular user. Processes that are started at boot time usually run as root or nobody. Processes that you start will run as you. Processes started as other users will run as those users.
You have control over all the processes that you start. Additionally, root has control over all processes on the system, including those started by other users. Processes can be controlled and monitored through several programs, as well as some shell commands.
11.1 Backgrounding
Programs started from the command line start up in the foreground. This allows you to see all the output of the program and interact with it. However, there are several occasions when you'd like the program to run without taking up your terminal. This is called running the program in the background, and there are a few ways to do it.
The first way to background a process is by adding an ampersand to the command line when you start the program. For example, assume you wanted to use the command line mp3 player amp to play a directory full of mp3s, but you needed to do something else on the same terminal. The following command line would start up amp in the background:
% amp *.mp3 &
The program will run as normal, and you are returned to a prompt.
The other way to background a process is to do so while it is running. First, start up a program. While it is running, hit Control+z. This suspends the process. A suspended process is basically paused. It momentarily stops running, but can be started up again at any time. Once you have suspended a process, you are returned to a prompt. You can background the process by typing:
% bg
Now the suspended process is running in the background.
http://www.slackbook.org/html/process-control.html
Slackware Linux Essentials: Tutorial 10
Chapter 10 Handling Files and Directories
Table of Contents
10.1 Navigation : ls, cd, and pwd
10.2 Pagers: more, less, and most
10.3 Simple Output: cat and echo
10.4 Creation: touch and mkdir
10.5 Copy and Move
10.6 Deletion: rm and rmdir
10.7 Aliasing files with ln
Linux aims to the most Unix-like it can be. Traditionally, Unix operating systems have been command-line oriented. We do have a graphical user interface in Slackware, but the command-line is still the main level of control for the system. Therefore, it is important to understand some of the basic file management commands.
The following sections explain the common file management commands and provide examples of how they are used. There are many other commands, but these will help you get started. Also, the commands are only briefly discussed here. You will find more detail in the accompanying man pages for each command.
10.1 Navigation : ls, cd, and pwd
10.1.1 ls
This command lists files in a directory. Windows and DOS users will notice its similarity to the dir command. By itself, ls(1) will list the files in the current directory. To see what's in your root directory, you could issue these commands:
% cd /
% ls
bin cdr dev home lost+found proc sbin tmp var
boot cdrom etc lib mnt root suncd usr vmlinuz
The problem a lot of people have with that output is that you cannot easily tell what is a directory and what is a file. Some users prefer that ls add a type identifier to each listing, like this:
% ls -FC
bin/ cdr/ dev/ home/ lost+found/ proc/ sbin/ tmp/ var/
boot/ cdrom/ etc/ lib/ mnt/ root/ suncd/ usr/ vmlinuz
Directories get a slash at the end of the name, executable files get an asterisk at the end of the name, and so on.
ls can also be used to get other statistics on files. For example, to see the creation dates, owners, and permissions, you would look at a long listing:
% ls -l
drwxr-xr-x 2 root bin 4096 May 7 09:11 bin/
drwxr-xr-x 2 root root 4096 Feb 24 03:55 boot/
drwxr-xr-x 2 root root 4096 Feb 18 01:10 cdr/
drwxr-xr-x 14 root root 6144 Oct 23 18:37 cdrom/
drwxr-xr-x 4 root root 28672 Mar 5 18:01 dev/
drwxr-xr-x 10 root root 4096 Mar 8 03:32 etc/
drwxr-xr-x 8 root root 4096 Mar 8 03:31 home/
drwxr-xr-x 3 root root 4096 Jan 23 21:29 lib/
drwxr-xr-x 2 root root 16384 Nov 1 08:53 lost+found/
drwxr-xr-x 2 root root 4096 Oct 6 12:47 mnt/
dr-xr-xr-x 62 root root 0 Mar 4 15:32 proc/
drwxr-x--x 12 root root 4096 Feb 26 02:06 root/
drwxr-xr-x 2 root bin 4096 Feb 17 02:02 sbin/
drwxr-xr-x 5 root root 2048 Oct 25 10:51 suncd/
drwxrwxrwt 4 root root 487424 Mar 7 20:42 tmp/
drwxr-xr-x 21 root root 4096 Aug 24 03:04 usr/
drwxr-xr-x 18 root root 4096 Mar 8 03:32 var/
Suppose you want to get a listing of the hidden files in the current directory. This command will do just that:
% ls -a
. bin cdrom home mnt sbin usr
.. boot dev lib proc suncd var
.pwrchute_tmp cdr etc lost+found root tmp vmlinuz
Files beginning with a period (called dot files) are hidden when you run ls. You will only see them if you pass the -a option.
There are many more options that can be found in the online manual page. Don't forget that you can combine options that you pass to ls.
10.1.2 cd
The cd command is used to change working directories. You simply type cd followed by the path name to change to. Here are some examples:
darkstar:~$ cd /bin
darkstar:/bin$ cd usr
bash: cd: usr: No such file or directory
darkstar:/bin$ cd /usr
darkstar:/usr$ ls
bin
darkstar:/usr$ cd bin
darkstar:/usr/bin$
Notice that without the preceding slash, it tries to change to a directory in the current directory. Also executing cd with no options will move you to your home directory.
The cd command is not like the other commands. It is a builtin shell command. Shell builtins are discussed in Section 8.3.1. This may not make any sense to you right now. Basically it means there is no man page for this command. Instead, you have to use the shell help. Like this:
% help cd
It will display the options for cd and how to use them.
10.1.3 pwd
The pwd command is used to show your current location. To use the pwd command just type pwd. For example:
% cd /bin
% pwd
/bin
% cd /usr
% cd bin
% pwd
/usr/bin
http://www.slackbook.org/html/file-commands.html
Table of Contents
10.1 Navigation : ls, cd, and pwd
10.2 Pagers: more, less, and most
10.3 Simple Output: cat and echo
10.4 Creation: touch and mkdir
10.5 Copy and Move
10.6 Deletion: rm and rmdir
10.7 Aliasing files with ln
Linux aims to the most Unix-like it can be. Traditionally, Unix operating systems have been command-line oriented. We do have a graphical user interface in Slackware, but the command-line is still the main level of control for the system. Therefore, it is important to understand some of the basic file management commands.
The following sections explain the common file management commands and provide examples of how they are used. There are many other commands, but these will help you get started. Also, the commands are only briefly discussed here. You will find more detail in the accompanying man pages for each command.
10.1 Navigation : ls, cd, and pwd
10.1.1 ls
This command lists files in a directory. Windows and DOS users will notice its similarity to the dir command. By itself, ls(1) will list the files in the current directory. To see what's in your root directory, you could issue these commands:
% cd /
% ls
bin cdr dev home lost+found proc sbin tmp var
boot cdrom etc lib mnt root suncd usr vmlinuz
The problem a lot of people have with that output is that you cannot easily tell what is a directory and what is a file. Some users prefer that ls add a type identifier to each listing, like this:
% ls -FC
bin/ cdr/ dev/ home/ lost+found/ proc/ sbin/ tmp/ var/
boot/ cdrom/ etc/ lib/ mnt/ root/ suncd/ usr/ vmlinuz
Directories get a slash at the end of the name, executable files get an asterisk at the end of the name, and so on.
ls can also be used to get other statistics on files. For example, to see the creation dates, owners, and permissions, you would look at a long listing:
% ls -l
drwxr-xr-x 2 root bin 4096 May 7 09:11 bin/
drwxr-xr-x 2 root root 4096 Feb 24 03:55 boot/
drwxr-xr-x 2 root root 4096 Feb 18 01:10 cdr/
drwxr-xr-x 14 root root 6144 Oct 23 18:37 cdrom/
drwxr-xr-x 4 root root 28672 Mar 5 18:01 dev/
drwxr-xr-x 10 root root 4096 Mar 8 03:32 etc/
drwxr-xr-x 8 root root 4096 Mar 8 03:31 home/
drwxr-xr-x 3 root root 4096 Jan 23 21:29 lib/
drwxr-xr-x 2 root root 16384 Nov 1 08:53 lost+found/
drwxr-xr-x 2 root root 4096 Oct 6 12:47 mnt/
dr-xr-xr-x 62 root root 0 Mar 4 15:32 proc/
drwxr-x--x 12 root root 4096 Feb 26 02:06 root/
drwxr-xr-x 2 root bin 4096 Feb 17 02:02 sbin/
drwxr-xr-x 5 root root 2048 Oct 25 10:51 suncd/
drwxrwxrwt 4 root root 487424 Mar 7 20:42 tmp/
drwxr-xr-x 21 root root 4096 Aug 24 03:04 usr/
drwxr-xr-x 18 root root 4096 Mar 8 03:32 var/
Suppose you want to get a listing of the hidden files in the current directory. This command will do just that:
% ls -a
. bin cdrom home mnt sbin usr
.. boot dev lib proc suncd var
.pwrchute_tmp cdr etc lost+found root tmp vmlinuz
Files beginning with a period (called dot files) are hidden when you run ls. You will only see them if you pass the -a option.
There are many more options that can be found in the online manual page. Don't forget that you can combine options that you pass to ls.
10.1.2 cd
The cd command is used to change working directories. You simply type cd followed by the path name to change to. Here are some examples:
darkstar:~$ cd /bin
darkstar:/bin$ cd usr
bash: cd: usr: No such file or directory
darkstar:/bin$ cd /usr
darkstar:/usr$ ls
bin
darkstar:/usr$ cd bin
darkstar:/usr/bin$
Notice that without the preceding slash, it tries to change to a directory in the current directory. Also executing cd with no options will move you to your home directory.
The cd command is not like the other commands. It is a builtin shell command. Shell builtins are discussed in Section 8.3.1. This may not make any sense to you right now. Basically it means there is no man page for this command. Instead, you have to use the shell help. Like this:
% help cd
It will display the options for cd and how to use them.
10.1.3 pwd
The pwd command is used to show your current location. To use the pwd command just type pwd. For example:
% cd /bin
% pwd
/bin
% cd /usr
% cd bin
% pwd
/usr/bin
http://www.slackbook.org/html/file-commands.html
Slackware Linux Essentials: Tutorial 09
Chapter 9 Filesystem Structure
Table of Contents
9.1 Ownership
9.2 Permissions
9.3 Links
9.4 Mounting Devices
9.5 NFS Mounts
We have already discussed the directory structure in Slackware Linux. By this point, you should be able to find files and directories that you need. But there is more to the filesystem than just the directory structure.
Linux is a multiuser operating system. Every aspect of the system is multiuser, even the filesystem. The system stores information like who owns a file and who can read it. There are other unique parts about the filesystems, such as links and NFS mounts. This section explains these, as well as the multiuser aspects of the filesystem.
9.1 Ownership
The filesystem stores ownership information for each file and directory on the system. This includes what user and group own a particular file. The easiest way to see this information is with the ls command:
% ls -l /usr/bin/wc
-rwxr-xr-x 1 root bin 7368 Jul 30 1999 /usr/bin/wc
We are interested in the third and fourth columns. These contain the username and group name that owns this file. We see that the user “root” and the group “bin” own this file.
We can easily change the file owners with the chown(1) (which means “change owner”) and chgrp(1) (which means “change group”) commands. To change the file owner to daemon, we would use chown:
# chown daemon /usr/bin/wc
To change the group owner to “root”, we would use chgrp:
# chgrp root /usr/bin/wc
We can also use chown to specify the user and group owners for a file:
# chown daemon:root /usr/bin/wc
In the above example, the user could have used a period instead of a colon. The result would have been the same; however, the colon is considered better form. Use of the period is deprecated and may be removed from future versions of chown to allow usernames with periods in them. These usernames tend to be very popular with Windows Exchange Servers and are encountered most commonly in email addresses such as: mr.jones@example.com. In slackware, administrators are advised to stay away from such usernames because some scripts still use the period to indicate the user and group of a file or directory. In our example, chmod would interpret mr.jones as user “mr” and group “jones”.
File ownership is a very important part of using a Linux system, even if you are the only user. You sometimes need to fix ownerships on files and device nodes.
http://www.slackbook.org/html/filesystem-structure.html
Table of Contents
9.1 Ownership
9.2 Permissions
9.3 Links
9.4 Mounting Devices
9.5 NFS Mounts
We have already discussed the directory structure in Slackware Linux. By this point, you should be able to find files and directories that you need. But there is more to the filesystem than just the directory structure.
Linux is a multiuser operating system. Every aspect of the system is multiuser, even the filesystem. The system stores information like who owns a file and who can read it. There are other unique parts about the filesystems, such as links and NFS mounts. This section explains these, as well as the multiuser aspects of the filesystem.
9.1 Ownership
The filesystem stores ownership information for each file and directory on the system. This includes what user and group own a particular file. The easiest way to see this information is with the ls command:
% ls -l /usr/bin/wc
-rwxr-xr-x 1 root bin 7368 Jul 30 1999 /usr/bin/wc
We are interested in the third and fourth columns. These contain the username and group name that owns this file. We see that the user “root” and the group “bin” own this file.
We can easily change the file owners with the chown(1) (which means “change owner”) and chgrp(1) (which means “change group”) commands. To change the file owner to daemon, we would use chown:
# chown daemon /usr/bin/wc
To change the group owner to “root”, we would use chgrp:
# chgrp root /usr/bin/wc
We can also use chown to specify the user and group owners for a file:
# chown daemon:root /usr/bin/wc
In the above example, the user could have used a period instead of a colon. The result would have been the same; however, the colon is considered better form. Use of the period is deprecated and may be removed from future versions of chown to allow usernames with periods in them. These usernames tend to be very popular with Windows Exchange Servers and are encountered most commonly in email addresses such as: mr.jones@example.com. In slackware, administrators are advised to stay away from such usernames because some scripts still use the period to indicate the user and group of a file or directory. In our example, chmod would interpret mr.jones as user “mr” and group “jones”.
File ownership is a very important part of using a Linux system, even if you are the only user. You sometimes need to fix ownerships on files and device nodes.
http://www.slackbook.org/html/filesystem-structure.html
Slackware Linux Essentials: Tutorial 08
Chapter 8 The Shell
Table of Contents
8.1 Users
8.2 The Command Line
8.3 The Bourne Again Shell (bash)
8.4 Virtual Terminals
In a graphical environment, the interface is provided by a program that creates windows, scrollbars, menus, etc. In a commandline environment, the user interface is provided by a shell, which interprets commands and generally makes things useable. Immediately after logging in (which is covered in this chapter), users are put into a shell and allowed to go about their business. This chapter serves as an introduction to the shell, and to the most common shell among Linux users-- the Bourne Again Shell (bash). For more detailed information on anything in this chapter, check out the bash(1) man page.
8.1 Users
8.1.1 Logging In
So you've booted, and you're looking at something that looks like this:
Welcome to Linux 2.4.18
Last login: Wed Jan 1 15:59:14 -0500 2005 on tty6.
darkstar login:
Hmm.. nobody said anything about a login. And what's a darkstar? Don't worry; you probably didn't accidentally fire up a hyperspace comm-link to the Empire's artificial moon. (I'm afraid the hyperspace comm-link protocol isn't currently supported by the Linux kernel. Maybe the 2.8 kernel branch will at last provide this oft looked-for support.) No, darkstar is just the name of one of our computers, and its name gets stamped on as the default. If you specified a name for your computer during setup, you should see it instead of darkstar.
As for the login... If this is your first time, you'll want to log in as root. You'll be prompted for a password; if you set one during the setup process, that's what it's looking for. If not, just hit enter. That's it-- you're in!
8.1.2 Root: The Superuser
Okay, who or what is root? And what's it doing with an account on your system?
Well, in the world of Unix and similar operating systems (like Linux), there are users and then there are users. We'll go into this in more detail later, but the important thing to know now is that root is the user above all users; root is all-powerful and all-knowing, and nobody disobeys root. It just isn't allowed. root is what we call a “superuser”, and rightly so. And best of all, root is you.
Cool, huh?
If you're not sure: yes, that's very cool. The catch is, though, that root is inherently allowed to break anything it so desires. You might want to skip ahead to Section 12.1.1 and see about adding a user; then login as that user and work from there. The traditional wisdom is that it's best to only become the superuser when absolutely necessary, so as to minimize the possibility of accidentally breaking something.
By the way, if you decide you want to be root while you're logged in as someone else, no problem. Just use the su(1) command. You'll be asked for root's password and then it will make you root until you exit or logout. You can also become any other user using su, provided you know that user's password: su logan, for instance, would make you me.
root is allowed to su to any user, without requiring their password.
http://www.slackbook.org/html/shell.html
Table of Contents
8.1 Users
8.2 The Command Line
8.3 The Bourne Again Shell (bash)
8.4 Virtual Terminals
In a graphical environment, the interface is provided by a program that creates windows, scrollbars, menus, etc. In a commandline environment, the user interface is provided by a shell, which interprets commands and generally makes things useable. Immediately after logging in (which is covered in this chapter), users are put into a shell and allowed to go about their business. This chapter serves as an introduction to the shell, and to the most common shell among Linux users-- the Bourne Again Shell (bash). For more detailed information on anything in this chapter, check out the bash(1) man page.
8.1 Users
8.1.1 Logging In
So you've booted, and you're looking at something that looks like this:
Welcome to Linux 2.4.18
Last login: Wed Jan 1 15:59:14 -0500 2005 on tty6.
darkstar login:
Hmm.. nobody said anything about a login. And what's a darkstar? Don't worry; you probably didn't accidentally fire up a hyperspace comm-link to the Empire's artificial moon. (I'm afraid the hyperspace comm-link protocol isn't currently supported by the Linux kernel. Maybe the 2.8 kernel branch will at last provide this oft looked-for support.) No, darkstar is just the name of one of our computers, and its name gets stamped on as the default. If you specified a name for your computer during setup, you should see it instead of darkstar.
As for the login... If this is your first time, you'll want to log in as root. You'll be prompted for a password; if you set one during the setup process, that's what it's looking for. If not, just hit enter. That's it-- you're in!
8.1.2 Root: The Superuser
Okay, who or what is root? And what's it doing with an account on your system?
Well, in the world of Unix and similar operating systems (like Linux), there are users and then there are users. We'll go into this in more detail later, but the important thing to know now is that root is the user above all users; root is all-powerful and all-knowing, and nobody disobeys root. It just isn't allowed. root is what we call a “superuser”, and rightly so. And best of all, root is you.
Cool, huh?
If you're not sure: yes, that's very cool. The catch is, though, that root is inherently allowed to break anything it so desires. You might want to skip ahead to Section 12.1.1 and see about adding a user; then login as that user and work from there. The traditional wisdom is that it's best to only become the superuser when absolutely necessary, so as to minimize the possibility of accidentally breaking something.
By the way, if you decide you want to be root while you're logged in as someone else, no problem. Just use the su(1) command. You'll be asked for root's password and then it will make you root until you exit or logout. You can also become any other user using su, provided you know that user's password: su logan, for instance, would make you me.
root is allowed to su to any user, without requiring their password.
http://www.slackbook.org/html/shell.html
Slackware Linux Essentials: Tutorial 07
Chapter 7 Booting
Table of Contents
7.1 LILO
7.2 LOADLIN
7.3 Dual Booting
The process of booting your Linux system can sometimes be easy and sometimes be difficult. Many users install Slackware on their computer and that's it. They just turn it on and it's ready to use. Othertimes, simply booting the machine can be a chore. For most users, LILO works best. Slackware includes LILO and Loadlin for booting Slackware Linux. LILO will work from a hard drive partition, a hard drive's master boot record, or a floppy disk, making it a very versatile tool. Loadlin works from a DOS command line, killing DOS and invoking Linux.
Another popular utility for booting Linux is GRUB. GRUB is not included or officially supported by Slackware. Slackware holds to the “tried and true” standard for what gets included inside the distribution. While GRUB works well and includes some features that LILO does not, LILO handles all the essential tasks of a boot loader reliably with a proven track record. Being younger, GRUB hasn't quite lived up to that legacy yet. As it is not included with Slackware, we do not discuss it here. If you wish to use GRUB (perhaps it came with another Linux OS and you want to use it to dual-boot) consult GRUB's documentation.
This section covers using LILO and Loadlin, the two booters included with Slackware. It also explains some typical dual booting scenarios and how you could go about setting it up.
7.1 LILO
The Linux Loader, or LILO, is the most popular booter in use on Linux systems. It is quite configurable and can easily be used to boot other operating systems.
Slackware Linux comes with a menu-driven configuration utility called liloconfig. This program is first run during the setup process, but you can invoke it later by typing liloconfig at the prompt.
LILO reads its settings from the /etc/lilo.conf(5) file. It is not read each time you boot up, but instead is read each time you install LILO. LILO must be reinstalled to the boot sector each time you make a configuration change. Many LILO errors come from making changes to the lilo.conf file, but failing to re-run lilo to install these changes. liloconfig will help you build the configuration file so that you can install LILO for your system. If you prefer to edit /etc/lilo.conf by hand, then reinstalling LILO just involves typing /sbin/lilo (as root) at the prompt.
When you first invoke liloconfig, it will look like this:
Figure 7-1. liloconfig
If this is your first time setting up LILO, you should pick simple. Otherwise, you might find expert to be faster if you are familiar with LILO and Linux. Selecting simple will begin the LILO configuration.
If kernel frame buffer support is compiled into your kernel, liloconfig will ask which video resolution you would like to use. This is the resolution that is also used by the XFree86 frame buffer server. If you do not want the console to run in a special video mode, selecting normal will keep the standard 80x25 text mode in use.
The next part of the LILO configuration is selecting where you want it installed. This is probably the most important step. The list below explains the installation places:
Root
This option installs LILO to the beginning of your Linux root partition. This is the safest option if you have other operating systems on your computer. It ensures that any other booters are not overwritten. The disadvantage is that LILO will only load from here if your Linux drive is the first drive on your system. This is why many people chose to create a very small /boot partition as the first drive on their system. This allows the kernel and LILO to be installed at the beginning of the drive where LILO can find them. Previous versions of LILO contained an infamous flaw known as the “1024 cylinder limit”. LILO was unable to boot kernels on partitions past the 1024th cylinder. Recent editions of LILO have eliminated this problem.
Floppy
This method is even safer than the previous one. It creates a boot floppy that you can use to boot your Linux system. This keeps the booter off the hard disk entirely, so you only boot this floppy when you want to use Slackware. The flaws with this method are obvious. Floppies are notoriously fickle, prone to failures. Secondly, the boot loader is no longer self-contained within the computer. If you loose your floppy disk, you'll have to make another to boot your system.
MBR
You will want to use this method if Slackware is the only operating system on your computer, or if you will be using LILO to choose between multiple operating systems on your computer. This is the most preferred method for installing LILO and will work with almost any computer system.
This option will overwrite any other booter you have in the MBR.
After selecting the installation location, liloconfig will write the configuration file and install LILO. That's it. If you select the expert mode you will receive a special menu. This menu allows you to tweak the /etc/lilo.conf file, add other operating systems to your boot menu, and set LILO to pass special kernel parameters at boot time. The expert menu looks like this:
Figure 7-2. liloconfig Expert Menu
Whatever your system configuration is, setting up a working boot loader is easy. liloconfig makes setting it up a cinch.
http://www.slackbook.org/html/booting.html
Table of Contents
7.1 LILO
7.2 LOADLIN
7.3 Dual Booting
The process of booting your Linux system can sometimes be easy and sometimes be difficult. Many users install Slackware on their computer and that's it. They just turn it on and it's ready to use. Othertimes, simply booting the machine can be a chore. For most users, LILO works best. Slackware includes LILO and Loadlin for booting Slackware Linux. LILO will work from a hard drive partition, a hard drive's master boot record, or a floppy disk, making it a very versatile tool. Loadlin works from a DOS command line, killing DOS and invoking Linux.
Another popular utility for booting Linux is GRUB. GRUB is not included or officially supported by Slackware. Slackware holds to the “tried and true” standard for what gets included inside the distribution. While GRUB works well and includes some features that LILO does not, LILO handles all the essential tasks of a boot loader reliably with a proven track record. Being younger, GRUB hasn't quite lived up to that legacy yet. As it is not included with Slackware, we do not discuss it here. If you wish to use GRUB (perhaps it came with another Linux OS and you want to use it to dual-boot) consult GRUB's documentation.
This section covers using LILO and Loadlin, the two booters included with Slackware. It also explains some typical dual booting scenarios and how you could go about setting it up.
7.1 LILO
The Linux Loader, or LILO, is the most popular booter in use on Linux systems. It is quite configurable and can easily be used to boot other operating systems.
Slackware Linux comes with a menu-driven configuration utility called liloconfig. This program is first run during the setup process, but you can invoke it later by typing liloconfig at the prompt.
LILO reads its settings from the /etc/lilo.conf(5) file. It is not read each time you boot up, but instead is read each time you install LILO. LILO must be reinstalled to the boot sector each time you make a configuration change. Many LILO errors come from making changes to the lilo.conf file, but failing to re-run lilo to install these changes. liloconfig will help you build the configuration file so that you can install LILO for your system. If you prefer to edit /etc/lilo.conf by hand, then reinstalling LILO just involves typing /sbin/lilo (as root) at the prompt.
When you first invoke liloconfig, it will look like this:
Figure 7-1. liloconfig
If this is your first time setting up LILO, you should pick simple. Otherwise, you might find expert to be faster if you are familiar with LILO and Linux. Selecting simple will begin the LILO configuration.
If kernel frame buffer support is compiled into your kernel, liloconfig will ask which video resolution you would like to use. This is the resolution that is also used by the XFree86 frame buffer server. If you do not want the console to run in a special video mode, selecting normal will keep the standard 80x25 text mode in use.
The next part of the LILO configuration is selecting where you want it installed. This is probably the most important step. The list below explains the installation places:
Root
This option installs LILO to the beginning of your Linux root partition. This is the safest option if you have other operating systems on your computer. It ensures that any other booters are not overwritten. The disadvantage is that LILO will only load from here if your Linux drive is the first drive on your system. This is why many people chose to create a very small /boot partition as the first drive on their system. This allows the kernel and LILO to be installed at the beginning of the drive where LILO can find them. Previous versions of LILO contained an infamous flaw known as the “1024 cylinder limit”. LILO was unable to boot kernels on partitions past the 1024th cylinder. Recent editions of LILO have eliminated this problem.
Floppy
This method is even safer than the previous one. It creates a boot floppy that you can use to boot your Linux system. This keeps the booter off the hard disk entirely, so you only boot this floppy when you want to use Slackware. The flaws with this method are obvious. Floppies are notoriously fickle, prone to failures. Secondly, the boot loader is no longer self-contained within the computer. If you loose your floppy disk, you'll have to make another to boot your system.
MBR
You will want to use this method if Slackware is the only operating system on your computer, or if you will be using LILO to choose between multiple operating systems on your computer. This is the most preferred method for installing LILO and will work with almost any computer system.
This option will overwrite any other booter you have in the MBR.
After selecting the installation location, liloconfig will write the configuration file and install LILO. That's it. If you select the expert mode you will receive a special menu. This menu allows you to tweak the /etc/lilo.conf file, add other operating systems to your boot menu, and set LILO to pass special kernel parameters at boot time. The expert menu looks like this:
Figure 7-2. liloconfig Expert Menu
Whatever your system configuration is, setting up a working boot loader is easy. liloconfig makes setting it up a cinch.
http://www.slackbook.org/html/booting.html
Slackware Linux Essentials: Tutorial 06
Chapter 6 X Configuration
Table of Contents
6.1 xorgconfig
6.2 xorgsetup
6.3 xinitrc
6.4 xwmconfig
6.5 xdm
Starting with Slackware-10.0, the X Window environment in Slackware is provided by Xorg. X is responsible for providing a graphical user interface. It is independent from the operating system, unlike Windows or the MacOS.
The X Window System is implemented through many programs that run in userland. The two main components are the server and the window manager. The server provides the lowlevel functions for interacting with your video hardware, thus it is system specific. The window manager sits on top of the server and provides the user interface. The advantage to this is you can have many different graphical interfaces by simply changing the window manager you use.
Configuring X can be a complex task. The reason for this is the vast numbers of video cards available for the PC architecture, most of which use different programming interfaces. Luckily, most cards today support basic video standards known as VESA, and if your card is among them you'll be able to start X using the startx command right out of the box.
If this doesn't work with your card, or if you'd like to take advantage of the high-performance features of your video card such as hardware acceleration or 3-D hardware rendering, then you'll need to reconfigure X.
To configure X, you'll need to make an /etc/X11/xorg.conf file. This file contains lots of details about your video hardware, mouse, and monitor. It's a very complex configuration file, but fortunately there are several programs to help create one for you. We'll mention a few of them here.
6.1 xorgconfig
This is a simple menu driven frontend that's similar in feel to the Slackware installer. It simply tells the X server to take a look at the card, and then set up the best initial configuration file it can make based on the information it gathers. The generated /etc/X11/xorg.conf file should be a good starting point for most systems (and should work without modification).
This is a text-based X configuration program that's designed for the advanced system administrator. Here's a sample walkthrough using xorgconfig. First, start the program:
# xorgconfig
This will present a screenful of information about xorgconfig. To continue, press ENTER. xorgconfig will ask you to verify you have set your PATH correctly. It should be fine, so go ahead and hit ENTER.
Figure 6-1. xorgconfig Mouse Configuration
Select your mouse from the menu presented. If you don't see your serial mouse listed, pick the Microsoft protocol -- it's the most common and will probably work. Next xorgconfig will ask you about using ChordMiddle and Emulate3Buttons. You'll see these options described in detail on the screen. Use them if the middle button on your mouse doesn't work under X, or if your mouse only has two buttons (Emulate3Buttons lets you simulate the middle button by pressing both buttons simultaneously). Then, enter the name of your mouse device. The default choice, /dev/mouse, should work since the link was configured during Slackware setup. If you're running GPM (the Linux mouse server) in repeater mode, you can set your mouse type to /dev/gpmdata to have X get information about the mouse through gpm. In some cases (with busmice especially) this can work better, but most users shouldn't do this.
xorgconfig will ask you about enabling special key bindings. If you need this say “y”. Most users can say “n” -- enter this if you're not sure.
Figure 6-2. xorgconfig Horizontal Sync
In the next section you enter the sync range for your monitor. To start configuring your monitor, press ENTER. You will see a list of monitor types -- choose one of them. Be careful not to exceed the specifications of your monitor. Doing so could damage your hardware.
Figure 6-3. xorgconfig Vertical Sync
Specify the vertical sync range for your monitor (you should find this in the manual for the monitor). xorgconfig will ask you to enter strings to identify the monitor type in the xorg.conf file. Enter anything you like on these 3 lines (including nothing at all).
Figure 6-4. xorgconfig Video Card
Now you have the opportunity to look at the database of video card types. You'll want to do this, so say “y”, and select a card from the list shown. If you don't see your exact card, try selecting one that uses the same chipset and it will probably work fine.
Next, tell xorgconfig how much RAM you have on your video card. xorgconfig will want you to enter some more descriptive text about your video card. If you like, you can enter descriptions on these three lines.
You'll then be asked which display resolutions you want to use. Again, going with the provided defaults should be fine to start with. Later on, you can edit the /etc/X11/xorg.conf file and rearrange the modes so 1024x768 (or whatever mode you like) is the default.
At this point, the xorgconfig program will ask if you'd like to save the current configuration file. Answer yes, and the X configuration file is saved, completing the setup process. You can start X now with the startx command.
http://www.slackbook.org/html/x-window-system.html
Table of Contents
6.1 xorgconfig
6.2 xorgsetup
6.3 xinitrc
6.4 xwmconfig
6.5 xdm
Starting with Slackware-10.0, the X Window environment in Slackware is provided by Xorg. X is responsible for providing a graphical user interface. It is independent from the operating system, unlike Windows or the MacOS.
The X Window System is implemented through many programs that run in userland. The two main components are the server and the window manager. The server provides the lowlevel functions for interacting with your video hardware, thus it is system specific. The window manager sits on top of the server and provides the user interface. The advantage to this is you can have many different graphical interfaces by simply changing the window manager you use.
Configuring X can be a complex task. The reason for this is the vast numbers of video cards available for the PC architecture, most of which use different programming interfaces. Luckily, most cards today support basic video standards known as VESA, and if your card is among them you'll be able to start X using the startx command right out of the box.
If this doesn't work with your card, or if you'd like to take advantage of the high-performance features of your video card such as hardware acceleration or 3-D hardware rendering, then you'll need to reconfigure X.
To configure X, you'll need to make an /etc/X11/xorg.conf file. This file contains lots of details about your video hardware, mouse, and monitor. It's a very complex configuration file, but fortunately there are several programs to help create one for you. We'll mention a few of them here.
6.1 xorgconfig
This is a simple menu driven frontend that's similar in feel to the Slackware installer. It simply tells the X server to take a look at the card, and then set up the best initial configuration file it can make based on the information it gathers. The generated /etc/X11/xorg.conf file should be a good starting point for most systems (and should work without modification).
This is a text-based X configuration program that's designed for the advanced system administrator. Here's a sample walkthrough using xorgconfig. First, start the program:
# xorgconfig
This will present a screenful of information about xorgconfig. To continue, press ENTER. xorgconfig will ask you to verify you have set your PATH correctly. It should be fine, so go ahead and hit ENTER.
Figure 6-1. xorgconfig Mouse Configuration
Select your mouse from the menu presented. If you don't see your serial mouse listed, pick the Microsoft protocol -- it's the most common and will probably work. Next xorgconfig will ask you about using ChordMiddle and Emulate3Buttons. You'll see these options described in detail on the screen. Use them if the middle button on your mouse doesn't work under X, or if your mouse only has two buttons (Emulate3Buttons lets you simulate the middle button by pressing both buttons simultaneously). Then, enter the name of your mouse device. The default choice, /dev/mouse, should work since the link was configured during Slackware setup. If you're running GPM (the Linux mouse server) in repeater mode, you can set your mouse type to /dev/gpmdata to have X get information about the mouse through gpm. In some cases (with busmice especially) this can work better, but most users shouldn't do this.
xorgconfig will ask you about enabling special key bindings. If you need this say “y”. Most users can say “n” -- enter this if you're not sure.
Figure 6-2. xorgconfig Horizontal Sync
In the next section you enter the sync range for your monitor. To start configuring your monitor, press ENTER. You will see a list of monitor types -- choose one of them. Be careful not to exceed the specifications of your monitor. Doing so could damage your hardware.
Figure 6-3. xorgconfig Vertical Sync
Specify the vertical sync range for your monitor (you should find this in the manual for the monitor). xorgconfig will ask you to enter strings to identify the monitor type in the xorg.conf file. Enter anything you like on these 3 lines (including nothing at all).
Figure 6-4. xorgconfig Video Card
Now you have the opportunity to look at the database of video card types. You'll want to do this, so say “y”, and select a card from the list shown. If you don't see your exact card, try selecting one that uses the same chipset and it will probably work fine.
Next, tell xorgconfig how much RAM you have on your video card. xorgconfig will want you to enter some more descriptive text about your video card. If you like, you can enter descriptions on these three lines.
You'll then be asked which display resolutions you want to use. Again, going with the provided defaults should be fine to start with. Later on, you can edit the /etc/X11/xorg.conf file and rearrange the modes so 1024x768 (or whatever mode you like) is the default.
At this point, the xorgconfig program will ask if you'd like to save the current configuration file. Answer yes, and the X configuration file is saved, completing the setup process. You can start X now with the startx command.
http://www.slackbook.org/html/x-window-system.html
Slackware Linux Essentials: Tutorial 05
Chapter 5 Network Configuration
Table of Contents
5.1 Introduction: netconfig is your friend.
5.2 Network Hardware Configuration
5.3 TCP/IP Configuration
5.4 PPP
5.5 Wireless
5.6 Network File Systems
5.1 Introduction: netconfig is your friend.
When you initially installed Slackware, the setup program invoked the netconfig program. netconfig attempted to perform the following functions for you:
•It asked you for the name of your computer, and the domain name for your computer.
•It gave a brief explanation of the various types of addressing schemes, told when they should be used, and asked you which IP addressing scheme you wished to use to configure your network card:
◦Static-IP
◦DHCP
◦Loopback
•It then offered to probe for a network card to configure.
netconfig will generally take care of about 80% of the work of configuring your LAN network connection if you will let it. Note that I would strongly suggest that you review your config file for a couple of reasons:
1.You should never trust a setup program to properly configure your computer. If you use a setup program, you should review the configuration yourself.
2.If you are still learning Slackware and Linux system management, viewing a working configuration can be helpful. You'll at least know what the configuration should look like. This will allow you to correct problems due to misconfiguration of the system at a later date.
http://www.slackbook.org/html/network-configuration.html
Table of Contents
5.1 Introduction: netconfig is your friend.
5.2 Network Hardware Configuration
5.3 TCP/IP Configuration
5.4 PPP
5.5 Wireless
5.6 Network File Systems
5.1 Introduction: netconfig is your friend.
When you initially installed Slackware, the setup program invoked the netconfig program. netconfig attempted to perform the following functions for you:
•It asked you for the name of your computer, and the domain name for your computer.
•It gave a brief explanation of the various types of addressing schemes, told when they should be used, and asked you which IP addressing scheme you wished to use to configure your network card:
◦Static-IP
◦DHCP
◦Loopback
•It then offered to probe for a network card to configure.
netconfig will generally take care of about 80% of the work of configuring your LAN network connection if you will let it. Note that I would strongly suggest that you review your config file for a couple of reasons:
1.You should never trust a setup program to properly configure your computer. If you use a setup program, you should review the configuration yourself.
2.If you are still learning Slackware and Linux system management, viewing a working configuration can be helpful. You'll at least know what the configuration should look like. This will allow you to correct problems due to misconfiguration of the system at a later date.
http://www.slackbook.org/html/network-configuration.html
Slackware Linux Essentials: Tutorial 04
Chapter 4 System Configuration
Table of Contents
4.1 System Overview
4.2 Selecting a Kernel
Before you can configure the more advanced parts of your system, it's a good idea to learn how the system is organized and what commands can be used to search for files and programs. It's also good to know if you need to compile a custom kernel and what the steps for doing that are. This chapter will familiarize you with system organization and configuration files. Then, you can move on to configuring the more advanced parts of the system.
4.1 System Overview
It's important to understand how a Linux system is put together before diving into the various configuration aspects. A Linux system is significantly different from a DOS, Windows, or Macintosh system (with the exception of the Unix-based Mac OS X), but these sections will help you get acquainted with the layout so that you can easily configure your system to meet your needs.
4.1.1 File System Layout
The first noticeable difference between Slackware Linux and a DOS or Windows system is the filesystem. For starters, we do not use drive letters to denote different partitions. Under Linux, there is one main directory. You can relate this to the C: drive under DOS. Each partition on your system is mounted to a directory on the main directory. It's kind of like an ever-expanding hard disk.
We call the main directory the root directory, and it's denoted with a single slash (/). This concept may seem strange, but it actually makes life easy for you when you want to add more space. For example, let's say you run out of space on the drive that has /home on it. Most people install Slackware and make one big root drive. Well, since a partition can be mounted to any directory, you can simply go to the store and pick up a new hard drive and mount it to /home. You've now grafted on some more space to your system. And all without having to move many things around.
Below, you will find descriptions of the major top level directories under Slackware.
bin
Essential user programs are stored here. These represent the bare minimum set of programs required for a user to use the system. Things like the shell and the filesystem commands (ls, cp, and so on) are stored here. The /bin directory usually doesn't receive modification after installation. If it does, it's usually in the form of package upgrades that we provide.
boot
Files that are used by the Linux Loader (LILO). This directory also receives little modification after an installation. The kernel is stored here as of Slackware 8.1. In earlier releases of Slackware, the kernel was simply stored under / , but common practice is to put the kernel and related files here to facilitate dual-booting.
dev
Everything in Linux is treated as a file, even hardware devices like serial ports, hard disks, and scanners. In order to access these devices, a special file called a device node has to be present. All device nodes are stored in the /dev directory. You will find this to be true across many Unix-like operating systems.
etc
This directory holds system configuration files. Everything from the X Window configuration file, the user database, to the system startup scripts. The system administrator will become quite familiar with this directory over time.
home
Linux is a multiuser operating system. Each user on the system is given an account and a unique directory for personal files. This directory is called the user's home directory. The /home directory is provided as the default location for user home directories.
lib
System libraries that are required for basic operation are stored here. The C library, the dynamic loader, the ncurses library, and kernel modules are among the things stored here.
mnt
This directory contains temporary mount points for working on hard disks or removable drives. Here you'll find mount points for your CD-ROM and floppy drives.
opt
Optional software packages. The idea behind /opt is that each software package installs to /opt/software-package, which makes it easy to remove later. Slackware distributes some things in /opt (such as KDE in /opt/kde), but you are free to add anything you want to /opt.
proc
This is a unique directory. It's not really part of the filesystem, but a virtual filesystem that provides access to kernel information. Various pieces of information that the kernel wants you to know are conveyed to you through files in the /proc directory. You can also send information to the kernel through some of these files. Try doing cat /proc/cpuinfo.
root
The system administrator is known as root on the system. root's home directory is kept in /root instead of /home/root. The reason is simple. What if /home was a different partition from / and it could not be mounted? root would naturally want to log in and repair the problem. If his home directory was on the damaged filesystem, it would make it difficult for him to log in.
sbin
Essential programs that are run by root and during the system bootup process are kept here. Normal users will not run programs in this directory.
tmp
The temporary storage location. All users have read and write access to this directory.
usr
This is the big directory on a Linux system. Everything else pretty much goes here, programs, documentation, the kernel source code, and the X Window system. This is the directory to which you will most likely be installing programs.
var
System log files, cache data, and program lock files are stored here. This is the directory for frequently-changing data.
You should now have a good feel for which directories contain what on the filesystem. More detailed information about the filesystem layout is available in the hier(7) man page. The next section will help you find specific files easily, so you don't have to do it by hand.
4.1.2 Finding Files
You now know what each major directory holds, but it still doesn't really help you find things. I mean, you could go looking through directories, but there are quicker ways. There are four main file search commands available in Slackware.
4.1.2.1 which
The first is the which(1) command. which is usually used to locate a program quickly. It just searches your PATH and returns the first instance it finds and the directory path to it. Take this example:
% which bash
/bin/bash
From that you see that bash is in the /bin directory. This is a very limited command for searching, since it only searches your PATH.
4.1.2.2 whereis
The whereis(1) command works similar to which, but can also search for man pages and source files. A whereis search for bash should return this:
% whereis bash
bash: /bin/bash /usr/bin/bash /usr/man/man1/bash.1.gz
This command not only told us where the actual program is located, but also where the online documentation is stored. Still, this command is limited. What if you wanted to search for a specific configuration file? You can't use which or whereis for that.
4.1.2.3 find
The find(1) command allows the user to search the filesystem with a rich collection of search predicates. Users may specify a search with filename wildcards, ranges of modification or creation times, or other advanced properties. For example, to search for the default xinitrc file on the system, the following command could be used.
% find / -name xinitrc
/var/X11R6/lib/xinit/xinitrc
find will take a while to run, since it has to traverse the entire root directory tree. And if this command is run as a normal user, there will be permission denied error messages for directories that only root can see. But find found our file, so that's good. If only it could be a bit faster...
4.1.2.4 slocate
The slocate(1) command searches the entire filesystem, just like the find command can do, but it searches a database instead of the actual filesystem. The database is set to automatically update every morning, so you have a somewhat fresh listing of files on your system. You can manually run updatedb(1) to update the slocate database (before running updatedb by hand, you must first su to the root user). Here's an example of slocate in action:
% slocate xinitrc # we don't have to go to the root
/var/X11R6/lib/xinit/xinitrc
/var/X11R6/lib/xinit/xinitrc.fvwm2
/var/X11R6/lib/xinit/xinitrc.openwin
/var/X11R6/lib/xinit/xinitrc.twm
We got more than what we were looking for, and quickly too. With these commands, you should be able to find whatever you're looking for on your Linux system.
4.1.3 The /etc/rc.d Directory
The system initialization files are stored in the /etc/rc.d directory. Slackware uses the BSD-style layout for its initialization files as opposed to System V init scripts, which tend to make configuration changes much more difficult without using a program specifically designed for that purpose. In BSD-init scripts, each runlevel is given a single rc file. In System V, each runlevel is given its own directory, each containing numerous init scripts. This provides an organized structure that is easy to maintain.
There are several categories of initialization files. These are system startup, runlevels, network initialization, and System V compatibility. As per tradition, we'll lump everything else into another category.
4.1.3.1 System Startup
The first program to run under Slackware besides the Linux kernel is init(8). This program reads the /etc/inittab(5) file to see how to run the system. It runs the /etc/rc.d/rc.S script to prepare the system before going into your desired runlevel. The rc.S file enables your virtual memory, mounts your filesystems, cleans up certain log directories, initializes Plug and Play devices, loads kernel modules, configures PCMCIA devices, sets up serial ports, and runs System V init scripts (if found). Obviously rc.S has a lot on its plate, but here are some scripts in /etc/rc.d that rc.S will call on to complete its work:
rc.S
This is the actual system initialization script.
rc.modules
Loads kernel modules. Things like your network card, PPP support, and other things are loaded here. If this script finds rc.netdevice, it will run that as well.
rc.pcmcia
Probes for and configures any PCMCIA devices that you might have on your system. This is most useful for laptop users, who probably have a PCMCIA modem or network card.
rc.serial
Configures your serial ports by running the appropriate setserial commands.
rc.sysvinit
Looks for System V init scripts for the desired runlevel and runs them. This is discussed in more detail below.
4.1.3.2 Runlevel Initialization Scripts
After system initialization is complete, init moves on to runlevel initialization. A runlevel describes the state that your machine will be running in. Sound redundant? Well, the runlevel tells init if you will be accepting multiuser logins or just a single user, whether or not you want network services, and if you will be using the X Window System or agetty(8) to handle logins. The files below define the different runlevels in Slackware Linux.
rc.0
Halt the system (runlevel 0). By default, this is symlinked to rc.6.
rc.4
Multiuser startup (runlevel 4), but in X11 with KDM, GDM, or XDM as the login manager.
rc.6
Reboot the system (runlevel 6).
rc.K
Startup in single user mode (runlevel 1).
rc.M
Multiuser mode (runlevels 2 and 3), but with the standard text-based login. This is the default runlevel in Slackware.
4.1.3.3 Network Initialization
Runlevels 2, 3, and 4 will start up the network services. The following files are responsible for the network initialization:
rc.inet1
Created by netconfig, this file is responsible for configuring the actual network interface.
rc.inet2
Runs after rc.inet1 and starts up basic network services.
rc.atalk
Starts up AppleTalk services.
rc.httpd
Starts up the Apache web server. Like a few other rc scripts, this one can also be used to stop and restart a service. rc.httpd takes arguments of stop, start, or restart.
rc.news
Starts up the news server.
4.1.3.4 System V Compatibility
System V init compatibility was introduced in Slackware 7.0. Many other Linux distributions make use of this style instead of the BSD style. Basically each runlevel is given a subdirectory for init scripts, whereas BSD style gives one init script to each runlevel.
The rc.sysvinit script will search for any System V init scripts you have in /etc/rc.d and run them, if the runlevel is appropriate. This is useful for certain commercial software packages that install System V init scripts
4.1.3.5 Other Files
The scripts described below are the other system initialization scripts. They are typically run from one of the major scripts above, so all you need to do is edit the contents.
rc.gpm
Starts up general purpose mouse services. Allows you to copy and paste at the Linux console. Occasionally, gpm will cause problems with the mouse when it is used under X windows. If you experience problems with the mouse under X, try taking away the executable permission from this file and stopping the gpm server.
rc.font
Loads the custom screen font for the console.
rc.local
Contains any specific startup commands for your system. This is empty after a fresh install, as it is reserved for local administrators. This script is run after all other initialization has taken place.
To enable a script, all you need to do is add the execute permissions to it with the chmod command. To disable a script, remove the execute permissions from it. For more information about chmod, see Section 9.2.
http://www.slackbook.org/html/system-configuration.html
Table of Contents
4.1 System Overview
4.2 Selecting a Kernel
Before you can configure the more advanced parts of your system, it's a good idea to learn how the system is organized and what commands can be used to search for files and programs. It's also good to know if you need to compile a custom kernel and what the steps for doing that are. This chapter will familiarize you with system organization and configuration files. Then, you can move on to configuring the more advanced parts of the system.
4.1 System Overview
It's important to understand how a Linux system is put together before diving into the various configuration aspects. A Linux system is significantly different from a DOS, Windows, or Macintosh system (with the exception of the Unix-based Mac OS X), but these sections will help you get acquainted with the layout so that you can easily configure your system to meet your needs.
4.1.1 File System Layout
The first noticeable difference between Slackware Linux and a DOS or Windows system is the filesystem. For starters, we do not use drive letters to denote different partitions. Under Linux, there is one main directory. You can relate this to the C: drive under DOS. Each partition on your system is mounted to a directory on the main directory. It's kind of like an ever-expanding hard disk.
We call the main directory the root directory, and it's denoted with a single slash (/). This concept may seem strange, but it actually makes life easy for you when you want to add more space. For example, let's say you run out of space on the drive that has /home on it. Most people install Slackware and make one big root drive. Well, since a partition can be mounted to any directory, you can simply go to the store and pick up a new hard drive and mount it to /home. You've now grafted on some more space to your system. And all without having to move many things around.
Below, you will find descriptions of the major top level directories under Slackware.
bin
Essential user programs are stored here. These represent the bare minimum set of programs required for a user to use the system. Things like the shell and the filesystem commands (ls, cp, and so on) are stored here. The /bin directory usually doesn't receive modification after installation. If it does, it's usually in the form of package upgrades that we provide.
boot
Files that are used by the Linux Loader (LILO). This directory also receives little modification after an installation. The kernel is stored here as of Slackware 8.1. In earlier releases of Slackware, the kernel was simply stored under / , but common practice is to put the kernel and related files here to facilitate dual-booting.
dev
Everything in Linux is treated as a file, even hardware devices like serial ports, hard disks, and scanners. In order to access these devices, a special file called a device node has to be present. All device nodes are stored in the /dev directory. You will find this to be true across many Unix-like operating systems.
etc
This directory holds system configuration files. Everything from the X Window configuration file, the user database, to the system startup scripts. The system administrator will become quite familiar with this directory over time.
home
Linux is a multiuser operating system. Each user on the system is given an account and a unique directory for personal files. This directory is called the user's home directory. The /home directory is provided as the default location for user home directories.
lib
System libraries that are required for basic operation are stored here. The C library, the dynamic loader, the ncurses library, and kernel modules are among the things stored here.
mnt
This directory contains temporary mount points for working on hard disks or removable drives. Here you'll find mount points for your CD-ROM and floppy drives.
opt
Optional software packages. The idea behind /opt is that each software package installs to /opt/software-package, which makes it easy to remove later. Slackware distributes some things in /opt (such as KDE in /opt/kde), but you are free to add anything you want to /opt.
proc
This is a unique directory. It's not really part of the filesystem, but a virtual filesystem that provides access to kernel information. Various pieces of information that the kernel wants you to know are conveyed to you through files in the /proc directory. You can also send information to the kernel through some of these files. Try doing cat /proc/cpuinfo.
root
The system administrator is known as root on the system. root's home directory is kept in /root instead of /home/root. The reason is simple. What if /home was a different partition from / and it could not be mounted? root would naturally want to log in and repair the problem. If his home directory was on the damaged filesystem, it would make it difficult for him to log in.
sbin
Essential programs that are run by root and during the system bootup process are kept here. Normal users will not run programs in this directory.
tmp
The temporary storage location. All users have read and write access to this directory.
usr
This is the big directory on a Linux system. Everything else pretty much goes here, programs, documentation, the kernel source code, and the X Window system. This is the directory to which you will most likely be installing programs.
var
System log files, cache data, and program lock files are stored here. This is the directory for frequently-changing data.
You should now have a good feel for which directories contain what on the filesystem. More detailed information about the filesystem layout is available in the hier(7) man page. The next section will help you find specific files easily, so you don't have to do it by hand.
4.1.2 Finding Files
You now know what each major directory holds, but it still doesn't really help you find things. I mean, you could go looking through directories, but there are quicker ways. There are four main file search commands available in Slackware.
4.1.2.1 which
The first is the which(1) command. which is usually used to locate a program quickly. It just searches your PATH and returns the first instance it finds and the directory path to it. Take this example:
% which bash
/bin/bash
From that you see that bash is in the /bin directory. This is a very limited command for searching, since it only searches your PATH.
4.1.2.2 whereis
The whereis(1) command works similar to which, but can also search for man pages and source files. A whereis search for bash should return this:
% whereis bash
bash: /bin/bash /usr/bin/bash /usr/man/man1/bash.1.gz
This command not only told us where the actual program is located, but also where the online documentation is stored. Still, this command is limited. What if you wanted to search for a specific configuration file? You can't use which or whereis for that.
4.1.2.3 find
The find(1) command allows the user to search the filesystem with a rich collection of search predicates. Users may specify a search with filename wildcards, ranges of modification or creation times, or other advanced properties. For example, to search for the default xinitrc file on the system, the following command could be used.
% find / -name xinitrc
/var/X11R6/lib/xinit/xinitrc
find will take a while to run, since it has to traverse the entire root directory tree. And if this command is run as a normal user, there will be permission denied error messages for directories that only root can see. But find found our file, so that's good. If only it could be a bit faster...
4.1.2.4 slocate
The slocate(1) command searches the entire filesystem, just like the find command can do, but it searches a database instead of the actual filesystem. The database is set to automatically update every morning, so you have a somewhat fresh listing of files on your system. You can manually run updatedb(1) to update the slocate database (before running updatedb by hand, you must first su to the root user). Here's an example of slocate in action:
% slocate xinitrc # we don't have to go to the root
/var/X11R6/lib/xinit/xinitrc
/var/X11R6/lib/xinit/xinitrc.fvwm2
/var/X11R6/lib/xinit/xinitrc.openwin
/var/X11R6/lib/xinit/xinitrc.twm
We got more than what we were looking for, and quickly too. With these commands, you should be able to find whatever you're looking for on your Linux system.
4.1.3 The /etc/rc.d Directory
The system initialization files are stored in the /etc/rc.d directory. Slackware uses the BSD-style layout for its initialization files as opposed to System V init scripts, which tend to make configuration changes much more difficult without using a program specifically designed for that purpose. In BSD-init scripts, each runlevel is given a single rc file. In System V, each runlevel is given its own directory, each containing numerous init scripts. This provides an organized structure that is easy to maintain.
There are several categories of initialization files. These are system startup, runlevels, network initialization, and System V compatibility. As per tradition, we'll lump everything else into another category.
4.1.3.1 System Startup
The first program to run under Slackware besides the Linux kernel is init(8). This program reads the /etc/inittab(5) file to see how to run the system. It runs the /etc/rc.d/rc.S script to prepare the system before going into your desired runlevel. The rc.S file enables your virtual memory, mounts your filesystems, cleans up certain log directories, initializes Plug and Play devices, loads kernel modules, configures PCMCIA devices, sets up serial ports, and runs System V init scripts (if found). Obviously rc.S has a lot on its plate, but here are some scripts in /etc/rc.d that rc.S will call on to complete its work:
rc.S
This is the actual system initialization script.
rc.modules
Loads kernel modules. Things like your network card, PPP support, and other things are loaded here. If this script finds rc.netdevice, it will run that as well.
rc.pcmcia
Probes for and configures any PCMCIA devices that you might have on your system. This is most useful for laptop users, who probably have a PCMCIA modem or network card.
rc.serial
Configures your serial ports by running the appropriate setserial commands.
rc.sysvinit
Looks for System V init scripts for the desired runlevel and runs them. This is discussed in more detail below.
4.1.3.2 Runlevel Initialization Scripts
After system initialization is complete, init moves on to runlevel initialization. A runlevel describes the state that your machine will be running in. Sound redundant? Well, the runlevel tells init if you will be accepting multiuser logins or just a single user, whether or not you want network services, and if you will be using the X Window System or agetty(8) to handle logins. The files below define the different runlevels in Slackware Linux.
rc.0
Halt the system (runlevel 0). By default, this is symlinked to rc.6.
rc.4
Multiuser startup (runlevel 4), but in X11 with KDM, GDM, or XDM as the login manager.
rc.6
Reboot the system (runlevel 6).
rc.K
Startup in single user mode (runlevel 1).
rc.M
Multiuser mode (runlevels 2 and 3), but with the standard text-based login. This is the default runlevel in Slackware.
4.1.3.3 Network Initialization
Runlevels 2, 3, and 4 will start up the network services. The following files are responsible for the network initialization:
rc.inet1
Created by netconfig, this file is responsible for configuring the actual network interface.
rc.inet2
Runs after rc.inet1 and starts up basic network services.
rc.atalk
Starts up AppleTalk services.
rc.httpd
Starts up the Apache web server. Like a few other rc scripts, this one can also be used to stop and restart a service. rc.httpd takes arguments of stop, start, or restart.
rc.news
Starts up the news server.
4.1.3.4 System V Compatibility
System V init compatibility was introduced in Slackware 7.0. Many other Linux distributions make use of this style instead of the BSD style. Basically each runlevel is given a subdirectory for init scripts, whereas BSD style gives one init script to each runlevel.
The rc.sysvinit script will search for any System V init scripts you have in /etc/rc.d and run them, if the runlevel is appropriate. This is useful for certain commercial software packages that install System V init scripts
4.1.3.5 Other Files
The scripts described below are the other system initialization scripts. They are typically run from one of the major scripts above, so all you need to do is edit the contents.
rc.gpm
Starts up general purpose mouse services. Allows you to copy and paste at the Linux console. Occasionally, gpm will cause problems with the mouse when it is used under X windows. If you experience problems with the mouse under X, try taking away the executable permission from this file and stopping the gpm server.
rc.font
Loads the custom screen font for the console.
rc.local
Contains any specific startup commands for your system. This is empty after a fresh install, as it is reserved for local administrators. This script is run after all other initialization has taken place.
To enable a script, all you need to do is add the execute permissions to it with the chmod command. To disable a script, remove the execute permissions from it. For more information about chmod, see Section 9.2.
http://www.slackbook.org/html/system-configuration.html
Slackware Linux Essentials: Tutorial 03
Chapter 3 Installation
Table of Contents
3.1 Getting Slackware
3.2 System Requirements
3.3 Partitioning
3.4 The setup Program
Before you can use Slackware Linux, you'll have to obtain and install it. Getting Slackware is as easy as purchasing it or downloading it for free over the Internet. Installing it is also easy as long as you have some basic knowledge about your computer and are willing to learn a few other things. The installation program itself is very much a step-by-step process. Because of this, you can be up and running very quickly. In fact, Slackware boasts one of the lowest installation times of any full-featured Linux distribution.
3.1 Getting Slackware
3.1.1 The Official Disc and Box Sets
The official Slackware Linux CD set is available from Slackware Linux, Inc. The CD set consists of 4 discs. The first disk contains all the software needed for a basic server install, and the X window system. The second cd is a “live” cd; that is, a bootable cd that installs into RAM and gives you a temporary installation to play around with or do a data or machine rescue. This cd also contains a few packages such as the KDE and GNOME desktop environments. A few other goodies are included on the second cd including many non-vital packages in the “extra” folder. The third and fourth CDs contain the source code to all of Slackware, along with the original edition of this book.
One may also purchase a boxed set that includes the 4 discs and a copy of this book, as well as lots of neat Slackware gear to show off your geek pride. CD subscriptions are available at a reduced rate also.
The preferred method for shopping for Slackware merchandise is online at the Slackware store.
http://store.slackware.com
You can also call or e-mail your order in.
Table 3-1. Slackware Linux, Inc. Contact Information
Method Contact Details
Telephone 1-(925) 674-0783
Website http://store.slackware.com
Email orders@slackware.com
Postal 1164 Claremont Drive, Brentwood, CA 94513
3.1.2 Via the Internet
Slackware Linux is also freely available over the Internet. You may email in your support questions, but higher priority will be given to those who have purchased the official CD set. With that said, we get a lot of e-mails and our time is rather limited. Before e-mailing for support consider reading Chapter 2 first.
The official Slackware Linux Project website is located at:
http://www.slackware.com/
The primary FTP location for Slackware Linux is:
ftp://ftp.slackware.com/pub/slackware/
Bear in mind that our ftp site, while open for general use, does not have unlimited bandwidth. Please consider using a mirror near you to download Slackware. An incomplete list of mirrors can be found on our site at http://www.slackware.com/getslack.
http://www.slackbook.org/html/installation.html
Table of Contents
3.1 Getting Slackware
3.2 System Requirements
3.3 Partitioning
3.4 The setup Program
Before you can use Slackware Linux, you'll have to obtain and install it. Getting Slackware is as easy as purchasing it or downloading it for free over the Internet. Installing it is also easy as long as you have some basic knowledge about your computer and are willing to learn a few other things. The installation program itself is very much a step-by-step process. Because of this, you can be up and running very quickly. In fact, Slackware boasts one of the lowest installation times of any full-featured Linux distribution.
3.1 Getting Slackware
3.1.1 The Official Disc and Box Sets
The official Slackware Linux CD set is available from Slackware Linux, Inc. The CD set consists of 4 discs. The first disk contains all the software needed for a basic server install, and the X window system. The second cd is a “live” cd; that is, a bootable cd that installs into RAM and gives you a temporary installation to play around with or do a data or machine rescue. This cd also contains a few packages such as the KDE and GNOME desktop environments. A few other goodies are included on the second cd including many non-vital packages in the “extra” folder. The third and fourth CDs contain the source code to all of Slackware, along with the original edition of this book.
One may also purchase a boxed set that includes the 4 discs and a copy of this book, as well as lots of neat Slackware gear to show off your geek pride. CD subscriptions are available at a reduced rate also.
The preferred method for shopping for Slackware merchandise is online at the Slackware store.
http://store.slackware.com
You can also call or e-mail your order in.
Table 3-1. Slackware Linux, Inc. Contact Information
Method Contact Details
Telephone 1-(925) 674-0783
Website http://store.slackware.com
Email orders@slackware.com
Postal 1164 Claremont Drive, Brentwood, CA 94513
3.1.2 Via the Internet
Slackware Linux is also freely available over the Internet. You may email in your support questions, but higher priority will be given to those who have purchased the official CD set. With that said, we get a lot of e-mails and our time is rather limited. Before e-mailing for support consider reading Chapter 2 first.
The official Slackware Linux Project website is located at:
http://www.slackware.com/
The primary FTP location for Slackware Linux is:
ftp://ftp.slackware.com/pub/slackware/
Bear in mind that our ftp site, while open for general use, does not have unlimited bandwidth. Please consider using a mirror near you to download Slackware. An incomplete list of mirrors can be found on our site at http://www.slackware.com/getslack.
http://www.slackbook.org/html/installation.html
Slackware Linux Essentials: Tutorial 02
Chapter 2 Help
Table of Contents
2.1 System Help
2.2 Online Help
Often there are times when you might need help with a specific command, setting up a program, or getting a piece of hardware to work. Maybe you simply want to understand a given command better, or see what other options are available to use with it. Luckily, there are a variety of ways that you can get the help you're looking for. When you install Slackware you have the option of installing packages from the “F” series which includes FAQs and HOWTOs. Programs also come with help about their options, configuration files, and usage.
2.1 System Help
2.1.1 man
The man command (short for “manual”) is the traditional form of online documentation in Unix and Linux operating systems. Comprised of specially formatted files, the “man pages”, are written for the vast majority of commands and are distributed with the software itself. Executing man somecommand will display the man page for (naturally) the command specified, in our example this would be the imaginary program somecommand.
As you might imagine, the amount of man pages can quickly add up, becoming overly confusing and seriously complicated, even for an advanced user. So, for this reason, man pages are grouped into enumerated sections. This system has been around for a very long time; enough so that you will often see commands, programs, and even programming library functions referred to with their man section number.
For example:
You might see a reference to man(1). The numbering tells you that “man” is documented in section 1 (user commands); you can specify that you want the section 1 man page for “man” with the command man 1 man. Specifying the section that man should look in is useful in the case of multiple items with the same name.
Table 2-1. Man Page Sections
Section Contents
Section 1 user commands (intro only)
Section 2 system calls
Section 3 C library calls
Section 4 devices (e.g., hd, sd)
Section 5 file formats and protocols (e.g., wtmp, /etc/passwd, nfs)
Section 6 games (intro only)
Section 7 conventions, macro packages, etc. (e.g., nroff, ascii)
Section 8 system administration (intro only)
In addition to man(1), there are the commands whatis(1) and apropos(1) available to you, whose shared purpose is to make it easier to find information in the man system.
The command whatis gives a very brief description of system commands, somewhat in the style of a pocket command reference.
Example:
% whatis whatis
whatis (1) - search the whatis database for complete words
The command apropos is used to search for a man page containing a given keyword.
Example:
% apropos wav
cdda2wav (1) - a sampling utility that dumps CD audio data into wav sound files
netwave_cs (4) - Xircom Creditcard Netwave device driver
oggdec (1) - simple decoder, Ogg Vorbis file to PCM audio file (WAV or RAW)
wavelan (4) - AT&T GIS WaveLAN ISA device driver
wavelan_cs (4) - AT&T GIS WaveLAN PCMCIA device driver
wvlan_cs (4) - Lucent WaveLAN/IEEE 802.11 device driver
If you'd like further information on any of these commands, read their man pages for the details. ;)
2.1.2 The /usr/doc Directory
The source for most packages that we build comes with some sort of documentation: README files, usage instructions, license files, etc. Any sort of documentation that comes with the source is included and installed on your system in the /usr/doc directory. Each program will (usually) install its own documentation in the order of:
/usr/doc/$program-$version
Where $program is the name of the program you are wanting to read about, and $version is (obviously) the appropriate version of software package installed on your system.
For example, to read the documentation for the command man(1) you would want to cd to:
% cd /usr/doc/man-$version
If reading the appropriate man page(s) doesn't provide you with enough information, or address what you're looking for in particular, the /usr/doc directory should be your next stop.
2.1.3 HOWTOs and mini-HOWTOs
It is in the truest spirit of the Open Source community that brings us to the HOWTO/mini-HOWTO collection. These files are exactly what they sound like - documents and guides describing how to do stuff. If you installed the HOWTO collection, the HOWTOs will be installed to /usr/doc/Linux-HOWTOs and the mini-HOWTOs to /usr/doc/Linux-mini-HOWTOs.
Also included in the same package series is a collection of FAQs, which is an acronym which stands for
Frequently
Asked
Questions
These documents are written in a “Question and answer” style for (surprise) Frequently Asked Questions. The FAQs can often be a very useful place to look if you're just looking for a “Quick Fix” to something. If you decide to install the FAQs during setup, you will find them installed to the /usr/doc/Linux-FAQs directory.
These files are well worth reading whenever you're not quite sure how to proceed with something. They cover an amazing range of topics, more often than not in a surprisingly detailed manner. Good stuff!
http://www.slackbook.org/html/help.html
Table of Contents
2.1 System Help
2.2 Online Help
Often there are times when you might need help with a specific command, setting up a program, or getting a piece of hardware to work. Maybe you simply want to understand a given command better, or see what other options are available to use with it. Luckily, there are a variety of ways that you can get the help you're looking for. When you install Slackware you have the option of installing packages from the “F” series which includes FAQs and HOWTOs. Programs also come with help about their options, configuration files, and usage.
2.1 System Help
2.1.1 man
The man command (short for “manual”) is the traditional form of online documentation in Unix and Linux operating systems. Comprised of specially formatted files, the “man pages”, are written for the vast majority of commands and are distributed with the software itself. Executing man somecommand will display the man page for (naturally) the command specified, in our example this would be the imaginary program somecommand.
As you might imagine, the amount of man pages can quickly add up, becoming overly confusing and seriously complicated, even for an advanced user. So, for this reason, man pages are grouped into enumerated sections. This system has been around for a very long time; enough so that you will often see commands, programs, and even programming library functions referred to with their man section number.
For example:
You might see a reference to man(1). The numbering tells you that “man” is documented in section 1 (user commands); you can specify that you want the section 1 man page for “man” with the command man 1 man. Specifying the section that man should look in is useful in the case of multiple items with the same name.
Table 2-1. Man Page Sections
Section Contents
Section 1 user commands (intro only)
Section 2 system calls
Section 3 C library calls
Section 4 devices (e.g., hd, sd)
Section 5 file formats and protocols (e.g., wtmp, /etc/passwd, nfs)
Section 6 games (intro only)
Section 7 conventions, macro packages, etc. (e.g., nroff, ascii)
Section 8 system administration (intro only)
In addition to man(1), there are the commands whatis(1) and apropos(1) available to you, whose shared purpose is to make it easier to find information in the man system.
The command whatis gives a very brief description of system commands, somewhat in the style of a pocket command reference.
Example:
% whatis whatis
whatis (1) - search the whatis database for complete words
The command apropos is used to search for a man page containing a given keyword.
Example:
% apropos wav
cdda2wav (1) - a sampling utility that dumps CD audio data into wav sound files
netwave_cs (4) - Xircom Creditcard Netwave device driver
oggdec (1) - simple decoder, Ogg Vorbis file to PCM audio file (WAV or RAW)
wavelan (4) - AT&T GIS WaveLAN ISA device driver
wavelan_cs (4) - AT&T GIS WaveLAN PCMCIA device driver
wvlan_cs (4) - Lucent WaveLAN/IEEE 802.11 device driver
If you'd like further information on any of these commands, read their man pages for the details. ;)
2.1.2 The /usr/doc Directory
The source for most packages that we build comes with some sort of documentation: README files, usage instructions, license files, etc. Any sort of documentation that comes with the source is included and installed on your system in the /usr/doc directory. Each program will (usually) install its own documentation in the order of:
/usr/doc/$program-$version
Where $program is the name of the program you are wanting to read about, and $version is (obviously) the appropriate version of software package installed on your system.
For example, to read the documentation for the command man(1) you would want to cd to:
% cd /usr/doc/man-$version
If reading the appropriate man page(s) doesn't provide you with enough information, or address what you're looking for in particular, the /usr/doc directory should be your next stop.
2.1.3 HOWTOs and mini-HOWTOs
It is in the truest spirit of the Open Source community that brings us to the HOWTO/mini-HOWTO collection. These files are exactly what they sound like - documents and guides describing how to do stuff. If you installed the HOWTO collection, the HOWTOs will be installed to /usr/doc/Linux-HOWTOs and the mini-HOWTOs to /usr/doc/Linux-mini-HOWTOs.
Also included in the same package series is a collection of FAQs, which is an acronym which stands for
Frequently
Asked
Questions
These documents are written in a “Question and answer” style for (surprise) Frequently Asked Questions. The FAQs can often be a very useful place to look if you're just looking for a “Quick Fix” to something. If you decide to install the FAQs during setup, you will find them installed to the /usr/doc/Linux-FAQs directory.
These files are well worth reading whenever you're not quite sure how to proceed with something. They cover an amazing range of topics, more often than not in a surprisingly detailed manner. Good stuff!
http://www.slackbook.org/html/help.html
Slackware Linux Essentials: Tutorial 01
Chapter 1: An Introduction to Slackware Linux
Table of Contents
1.1 What is Linux?
1.2 What is Slackware?
1.3 Open Source and Free Software
1.1 What is Linux?
Linus Torvalds started Linux, an operating system kernel, as a personal project in 1991. He started the project because he wanted to run a Unix-based operating system without spending a lot of money. In addition, he wanted to learn the ins and outs of the 386 processor. Linux was released free of charge to the public so that anyone could study it and make improvements under the General Public License. (See Section 1.3 and Appendix A for an explanation of the license.) Today, Linux has grown into a major player in the operating system market. It has been ported to run on a variety of system architectures, including HP/Compaq's Alpha, Sun's SPARC and UltraSPARC, and Motorola's PowerPC chips (through Apple Macintosh and IBM RS/6000 computers.) Hundreds, if not thousands, of programmers all over the world now develop Linux. It runs programs like Sendmail, Apache, and BIND, which are very popular software used to run Internet servers. It's important to remember that the term “Linux” really refers to the kernel - the core of the operating system. This core is responsible for controlling your computer's processor, memory, hard drives, and peripherals. That's all Linux really does: It controls the operations of your computer and makes sure that all of its programs behave. Various companies and individuals bundle the kernel and various programs together to make an operating system. We call each bundle a Linux distribution.
1.1.1 A Word on GNU
The Linux kernel project began as a solo endeavor by Linus Torvalds in 1991, but as Isaac Newton once said, “If I have seen further, it is by standing on the shoulders of giants.” When Linus Torvalds began the kernel the Free Software Foundation had already established the idea of collaborative software. They entitled their effort GNU, a recursive acronym that means simply “GNU's Not Unix”. GNU software ran atop the Linux kernel from day 1. Their compiler gcc was used to compile the kernel. Today many GNU tools from gcc to gnutar are still at the basis of every major Linux distribution. For this reason many of the Free Software Foundation's proponents fervently state that their work should be given the same credit as the Linux kernel. They strongly suggest that all Linux distributions should refer to themselves as GNU/Linux distributions.
This is the topic of many flamewars, surpassed only by the ancient vi versus emacs holy war. The purpose of this book is not to fan the fires of this heated discussion, but rather to clarify the terminology for neophytes. When one sees GNU/Linux it means a Linux distribution. When one sees Linux they can either be referring to the kernel, or to a distribution. It can be rather confusing. Typically the term GNU/Linux isn't used because it's a mouth full.
http://www.slackbook.org/html/introduction.html
Table of Contents
1.1 What is Linux?
1.2 What is Slackware?
1.3 Open Source and Free Software
1.1 What is Linux?
Linus Torvalds started Linux, an operating system kernel, as a personal project in 1991. He started the project because he wanted to run a Unix-based operating system without spending a lot of money. In addition, he wanted to learn the ins and outs of the 386 processor. Linux was released free of charge to the public so that anyone could study it and make improvements under the General Public License. (See Section 1.3 and Appendix A for an explanation of the license.) Today, Linux has grown into a major player in the operating system market. It has been ported to run on a variety of system architectures, including HP/Compaq's Alpha, Sun's SPARC and UltraSPARC, and Motorola's PowerPC chips (through Apple Macintosh and IBM RS/6000 computers.) Hundreds, if not thousands, of programmers all over the world now develop Linux. It runs programs like Sendmail, Apache, and BIND, which are very popular software used to run Internet servers. It's important to remember that the term “Linux” really refers to the kernel - the core of the operating system. This core is responsible for controlling your computer's processor, memory, hard drives, and peripherals. That's all Linux really does: It controls the operations of your computer and makes sure that all of its programs behave. Various companies and individuals bundle the kernel and various programs together to make an operating system. We call each bundle a Linux distribution.
1.1.1 A Word on GNU
The Linux kernel project began as a solo endeavor by Linus Torvalds in 1991, but as Isaac Newton once said, “If I have seen further, it is by standing on the shoulders of giants.” When Linus Torvalds began the kernel the Free Software Foundation had already established the idea of collaborative software. They entitled their effort GNU, a recursive acronym that means simply “GNU's Not Unix”. GNU software ran atop the Linux kernel from day 1. Their compiler gcc was used to compile the kernel. Today many GNU tools from gcc to gnutar are still at the basis of every major Linux distribution. For this reason many of the Free Software Foundation's proponents fervently state that their work should be given the same credit as the Linux kernel. They strongly suggest that all Linux distributions should refer to themselves as GNU/Linux distributions.
This is the topic of many flamewars, surpassed only by the ancient vi versus emacs holy war. The purpose of this book is not to fan the fires of this heated discussion, but rather to clarify the terminology for neophytes. When one sees GNU/Linux it means a Linux distribution. When one sees Linux they can either be referring to the kernel, or to a distribution. It can be rather confusing. Typically the term GNU/Linux isn't used because it's a mouth full.
http://www.slackbook.org/html/introduction.html
Choose and Register a Domain Name
Labels:
Domain
Find the best web address and protect it with domain name registration.
To do business on the Web, you'll need at least one domain name -- the .com or .net website identifier that has become so familiar (and sometimes annoying) in commercials and print advertising. You may want to use your business name as your domain name, with .com or .net tacked on at the end -- or you might pick a new domain name that you think will draw people to your site.
To help your website, and business, flourish, pick a domain name that:
- is easy for Web users to remember and find
- suggests the nature of your product or service
- serves as a strong trademark so competitors won't be able to use a business name or domain name similar to it, and
- is free of legal conflicts with trademarks belonging to other businesses.
Choosing a Domain Name
The best domain names are often the simple ones -- short, memorable, clever, and easy to spell and pronounce. Nevertheless, you must weigh the sometimes competing concerns of a Web-friendly name with the importance of obtaining trademark protection for the name you choose.
Can You Get Trademark Protection?
Straightforward domain names that describe a business's product or service are more difficult to protect as trademarks than distinctive and clever domain names. Many good domain names -- for instance, coffee.com, drugs.com, and business.com -- are not eligible for much trademark protection because they aren't unique; they identify whole categories of products or services. Likewise, domain names that use geographic identifiers or surnames are less likely to receive trademark protection -- unless your name happens to be Dr. Koop or something equally famous.
To do business on the Web, you'll need at least one domain name -- the .com or .net website identifier that has become so familiar (and sometimes annoying) in commercials and print advertising. You may want to use your business name as your domain name, with .com or .net tacked on at the end -- or you might pick a new domain name that you think will draw people to your site.
To help your website, and business, flourish, pick a domain name that:
- is easy for Web users to remember and find
- suggests the nature of your product or service
- serves as a strong trademark so competitors won't be able to use a business name or domain name similar to it, and
- is free of legal conflicts with trademarks belonging to other businesses.
Choosing a Domain Name
The best domain names are often the simple ones -- short, memorable, clever, and easy to spell and pronounce. Nevertheless, you must weigh the sometimes competing concerns of a Web-friendly name with the importance of obtaining trademark protection for the name you choose.
Can You Get Trademark Protection?
Straightforward domain names that describe a business's product or service are more difficult to protect as trademarks than distinctive and clever domain names. Many good domain names -- for instance, coffee.com, drugs.com, and business.com -- are not eligible for much trademark protection because they aren't unique; they identify whole categories of products or services. Likewise, domain names that use geographic identifiers or surnames are less likely to receive trademark protection -- unless your name happens to be Dr. Koop or something equally famous.
Best Broadband in Malaysia
Labels:
Best Broadband in Malaysia
Guess what, I just came back from PacketOne Networks (P1, for short) office located just beside the Federal Highway. What did I go there for? Simple enough, because they knew I am the upcoming Malaysia Problogger and invited me over to officiate the launching of their long awaited P1 W1MAX USB Modem!

This USB modem is what the folks there called the WIGGY. You can see this teaser which counts down to PC Fair day! This is something which all of you have been waiting for… and you just have to wait two more days to find out all the details you need in PC Fair.
But you are in luck today! I show you first hand photos of the much talked about P1 W1MAX USB Modem.
The USB Dongle comes in a little plastic case. It contains the USB modem, a manual and is encased within some shock absorbent material.

The USB Modem itself is sleek and sexy. This small modem definitely provides more mobility for P1 W1MAX and so much better compared to the current bulky DS-300 Modem.
Let’s plug this baby into my USB port.
So far so good. Once the modem is plugged it, it triggers the self installation program and installs the device drivers and the connection manager program. This is simple enough and was completed in a couple of minutes. What the heck, let’s connect now….
Darn, can’t connect. The connection status stays as “Scanning” (red light blinking) for forever… Hey, P1 WiMAX supports download of up to 30Mbps and upload of up to 7Mbps, but I am getting “Scanning…” only. Not too sure it is because my account is not activated yet (they told me I will need to wait until tomorrow noon for account activation), or my area is located at the fringe of the coverage area. I will give it another chance tomorrow and will also try this at another place.
More details of this modem can be found on Green Packet’s website under the name US-230

This USB modem is what the folks there called the WIGGY. You can see this teaser which counts down to PC Fair day! This is something which all of you have been waiting for… and you just have to wait two more days to find out all the details you need in PC Fair.
But you are in luck today! I show you first hand photos of the much talked about P1 W1MAX USB Modem.
The USB Dongle comes in a little plastic case. It contains the USB modem, a manual and is encased within some shock absorbent material.

The USB Modem itself is sleek and sexy. This small modem definitely provides more mobility for P1 W1MAX and so much better compared to the current bulky DS-300 Modem.
Let’s plug this baby into my USB port.
So far so good. Once the modem is plugged it, it triggers the self installation program and installs the device drivers and the connection manager program. This is simple enough and was completed in a couple of minutes. What the heck, let’s connect now….
Darn, can’t connect. The connection status stays as “Scanning” (red light blinking) for forever… Hey, P1 WiMAX supports download of up to 30Mbps and upload of up to 7Mbps, but I am getting “Scanning…” only. Not too sure it is because my account is not activated yet (they told me I will need to wait until tomorrow noon for account activation), or my area is located at the fringe of the coverage area. I will give it another chance tomorrow and will also try this at another place.
More details of this modem can be found on Green Packet’s website under the name US-230
How to Connect Two PCs with an Ethernet Crossover Cable
Networking Options
There are four reasonable ways to connect two PCs (both running Windows) by a single cable:
1. Connect an Ethernet crossover cable between the Ethernet network ports on the two PCs. (Easy)
2. Connect a FireWire cable between the FireWire ports on the two PCs. (Easy)
3. Connect a special USB link cable between the two PCs, along with some software. (Requires some fussing, some software, and a special cable.)
4. Connect a serial-port crossover cable (sometimes called a null modem cable) between the serial ports on the two PCs. (Requires a fair amount of fussing, works slowly, and sometimes won’t work at all for reasons that never come clear.)
Use an Ethernet Crossover Cable to Connect Two PCs
By far, the simplest, easiest, and cheapest connection between two PCs is through a Category 5 Ethernet crossover cable. If you’re using Windows 2000, Windows XP, or Windows Vista, it’s virtually automatic. In summary: You turn both PCs off, connect the crossover cable between the Ethernet port on one PC and the Ethernet port on the other, and then turn them on and boot up. In a couple of minutes, you should be connected. That’s all it takes!
An Ethernet crossover cable is a special variety of the familiar Category 5 Ethernet patch cable. It looks almost exactly like an ordinary Ethernet patch cable, but it will be labeled somehow so that you know it’s a crossover cable. Look for the abbreviation CRS embossed in the plug on each end or for a label of some other kind.
TIP: If you have a crossover cable that isn’t labeled, label it right now. If you mix them up later on and try to use a crossover cable instead of a regular Ethernet patch cable (or vise versa), you will not be able to make a connection!
What is a Crossover Cable?
What makes the cable a crossover cable? It doesn’t look any different physically, and it’s only different electrically. Old-timers may remember something called a null modem, which was used to connect PCs through their serial ports in ancient times. A crossover cable is a null modem for Ethernet ports rather than serial ports. It connects the output pins of one Ethernet port to the input pins of another and vice versa. No communication can happen between two PCs on a straight-through patch cable because with a straight-through cable, the two PCs’ input pins are connected together, as are the output pins. Inputs can’t talk to inputs, nor outputs to outputs. The crossover cable makes sure that inputs talk to outputs and outputs to inputs.
How to Create the Connection
Here’s your step-by-step for direct connection via Ethernet crossover cable:
1. Make sure the network ports on both PCs are enabled in pre-Vista PCs. To do this, click Start, then Settings, and then Network and Dial Up Connections. Look for a line labeled “Local Area Connection” and be sure that it’s marked as “Enabled.”
2. Make sure the cable in your hand is indeed a crossover cable, and connect it between the two Ethernet ports.
3. Power up or reboot both PCs.
Once both PCs are past bootup, give them a few minutes to self-assign an IP address with APIPA and locate one another.
4. For XP PCs, in Windows Explorer, expand My Network Places and click on Computers Near Me. Look and see if the name of the opposite PC is displayed. For Vista, open Network. If you don't see the new PC, click Network and Sharing Center and enable "discovery".
There are four reasonable ways to connect two PCs (both running Windows) by a single cable:
1. Connect an Ethernet crossover cable between the Ethernet network ports on the two PCs. (Easy)
2. Connect a FireWire cable between the FireWire ports on the two PCs. (Easy)
3. Connect a special USB link cable between the two PCs, along with some software. (Requires some fussing, some software, and a special cable.)
4. Connect a serial-port crossover cable (sometimes called a null modem cable) between the serial ports on the two PCs. (Requires a fair amount of fussing, works slowly, and sometimes won’t work at all for reasons that never come clear.)
Use an Ethernet Crossover Cable to Connect Two PCs
By far, the simplest, easiest, and cheapest connection between two PCs is through a Category 5 Ethernet crossover cable. If you’re using Windows 2000, Windows XP, or Windows Vista, it’s virtually automatic. In summary: You turn both PCs off, connect the crossover cable between the Ethernet port on one PC and the Ethernet port on the other, and then turn them on and boot up. In a couple of minutes, you should be connected. That’s all it takes!
An Ethernet crossover cable is a special variety of the familiar Category 5 Ethernet patch cable. It looks almost exactly like an ordinary Ethernet patch cable, but it will be labeled somehow so that you know it’s a crossover cable. Look for the abbreviation CRS embossed in the plug on each end or for a label of some other kind.
TIP: If you have a crossover cable that isn’t labeled, label it right now. If you mix them up later on and try to use a crossover cable instead of a regular Ethernet patch cable (or vise versa), you will not be able to make a connection!
What is a Crossover Cable?
What makes the cable a crossover cable? It doesn’t look any different physically, and it’s only different electrically. Old-timers may remember something called a null modem, which was used to connect PCs through their serial ports in ancient times. A crossover cable is a null modem for Ethernet ports rather than serial ports. It connects the output pins of one Ethernet port to the input pins of another and vice versa. No communication can happen between two PCs on a straight-through patch cable because with a straight-through cable, the two PCs’ input pins are connected together, as are the output pins. Inputs can’t talk to inputs, nor outputs to outputs. The crossover cable makes sure that inputs talk to outputs and outputs to inputs.
How to Create the Connection
Here’s your step-by-step for direct connection via Ethernet crossover cable:
1. Make sure the network ports on both PCs are enabled in pre-Vista PCs. To do this, click Start, then Settings, and then Network and Dial Up Connections. Look for a line labeled “Local Area Connection” and be sure that it’s marked as “Enabled.”
2. Make sure the cable in your hand is indeed a crossover cable, and connect it between the two Ethernet ports.
3. Power up or reboot both PCs.
Once both PCs are past bootup, give them a few minutes to self-assign an IP address with APIPA and locate one another.
4. For XP PCs, in Windows Explorer, expand My Network Places and click on Computers Near Me. Look and see if the name of the opposite PC is displayed. For Vista, open Network. If you don't see the new PC, click Network and Sharing Center and enable "discovery".
Connect Two Home Computers for File Sharing
Methods for networking two computers
The simplest kind of home network contains exactly two computers. You can use this kind of network to share files, a printer or another peripheral device, and even an Internet connection. To connect two computers for sharing these and other network resources, consider the options described below.
Connecting Two Computers Directly With Cable
The traditional method to network two computers involves making a dedicated link by plugging one cable into the two systems. Several alternatives exist for networking two computers in this manner:
•Ethernet crossover cable
•Null modem serial cable or parallel peripheral cable
•Special-purpose USB cables
Ethernet - Of the above choices, the Ethernet method is preferred as it supports a reliable, high-speed connection with minimal configuration required. Additionally, Ethernet technology offers the most general-purpose solution, allowing networks with more than two computers to be built fairly easily later. If one of your computers possesses an Ethernet adapter but the other has USB, an Ethernet crossover cable can still be used by first plugging a USB-to-Ethernet converter unit into the computer's USB port.
See also: Ethernet crossover cables
Serial and parallel - This type of cabling, called Direct Cable Connection (DCC) when using Microsoft Windows, offers lower performance but offers the same basic functionality as Ethernet cables. You may prefer this option if you have such cables readily available and network speed is not a concern. Serial and parallel cables are never used to network more than two computers.
USB - Ordinary USB cables must not be used to connect two computers directly to each other. Attempting to do so can electrically damage the computers! However, special USB cables designed for direct connection exist that can be used safely. You may prefer this option over others if your computers lack functional Ethernet network adapters.
To make dedicated connections with Ethernet, USB, serial or parallel cables requires
1. Each computer have a functioning network interface with an external jack for the cable, and
2. The network settings on each computer appropriately configured
One phone line or power cord cannot be used to directly connect two computers to each other for networking.
The simplest kind of home network contains exactly two computers. You can use this kind of network to share files, a printer or another peripheral device, and even an Internet connection. To connect two computers for sharing these and other network resources, consider the options described below.
Connecting Two Computers Directly With Cable
The traditional method to network two computers involves making a dedicated link by plugging one cable into the two systems. Several alternatives exist for networking two computers in this manner:
•Ethernet crossover cable
•Null modem serial cable or parallel peripheral cable
•Special-purpose USB cables
Ethernet - Of the above choices, the Ethernet method is preferred as it supports a reliable, high-speed connection with minimal configuration required. Additionally, Ethernet technology offers the most general-purpose solution, allowing networks with more than two computers to be built fairly easily later. If one of your computers possesses an Ethernet adapter but the other has USB, an Ethernet crossover cable can still be used by first plugging a USB-to-Ethernet converter unit into the computer's USB port.
See also: Ethernet crossover cables
Serial and parallel - This type of cabling, called Direct Cable Connection (DCC) when using Microsoft Windows, offers lower performance but offers the same basic functionality as Ethernet cables. You may prefer this option if you have such cables readily available and network speed is not a concern. Serial and parallel cables are never used to network more than two computers.
USB - Ordinary USB cables must not be used to connect two computers directly to each other. Attempting to do so can electrically damage the computers! However, special USB cables designed for direct connection exist that can be used safely. You may prefer this option over others if your computers lack functional Ethernet network adapters.
To make dedicated connections with Ethernet, USB, serial or parallel cables requires
1. Each computer have a functioning network interface with an external jack for the cable, and
2. The network settings on each computer appropriately configured
One phone line or power cord cannot be used to directly connect two computers to each other for networking.
Sharing your Internet Connection
Many people have multiple computers at their residence, however they typically have only one of the computers connected to the Internet if they are using high speed Internet access such as Cable Modem or DSL. The other computer is cursed to spend its days stuck on dial-up. Since I believe this is morally wrong, I wrote this article.
Despite what some Internet Companies (ISPs) would like you to think, you can (with the right equipment) connect all your computers over your single Internet connection. You do not have to pay any extra monthly fees and you will not loose any Internet functionality.
No matter how you decide to share your connection, it is going to require that you provide wiring or wireless to connect each computer. This can be done many different ways. Over your existing phone wires (slow but cheap), over network wires (very fast), or over wireless. After you get your network up and running then you can decide what method to share your Internet connection.
Clue: Sharing your Internet connection also provides a basic firewall to protect your PCs from intrusion or attack from the Internet.
Using a DSL/Cable Router
This is my recommended method for sharing an Internet connection. You have more flexibility and options with a router (such as port forwarding). To use a router there is one requirement, the DSL or Cable-modem connection must be an Ethernet connection, it cannot be a USB device that plugs into your computer. If you do have a USB DSL modem or Cable Modem your only choice is to make your computer the router (this is called Microsoft Internet Connection Sharing).
MS Internet Connection Sharing
Microsoft's ICS allows you to share any type of Internet connection, even if you want to share a Dial-Up. Using Internet Connection Sharing, which is built in to Windows XP/Me, is one way to get the job done. It basically requires one computer to have the Internet connection and a separate network card that is used to share to the rest of the network.
The downfalls are that this computer must be left on at all times because all the other computers rely on it for their Internet access, this computer must be equipped with 2 network connections (one to the Internet and one to the internal network) and ICS does not provide many features that come with using a router.
Despite what some Internet Companies (ISPs) would like you to think, you can (with the right equipment) connect all your computers over your single Internet connection. You do not have to pay any extra monthly fees and you will not loose any Internet functionality.
No matter how you decide to share your connection, it is going to require that you provide wiring or wireless to connect each computer. This can be done many different ways. Over your existing phone wires (slow but cheap), over network wires (very fast), or over wireless. After you get your network up and running then you can decide what method to share your Internet connection.
Clue: Sharing your Internet connection also provides a basic firewall to protect your PCs from intrusion or attack from the Internet.
Using a DSL/Cable Router
This is my recommended method for sharing an Internet connection. You have more flexibility and options with a router (such as port forwarding). To use a router there is one requirement, the DSL or Cable-modem connection must be an Ethernet connection, it cannot be a USB device that plugs into your computer. If you do have a USB DSL modem or Cable Modem your only choice is to make your computer the router (this is called Microsoft Internet Connection Sharing).
MS Internet Connection Sharing
Microsoft's ICS allows you to share any type of Internet connection, even if you want to share a Dial-Up. Using Internet Connection Sharing, which is built in to Windows XP/Me, is one way to get the job done. It basically requires one computer to have the Internet connection and a separate network card that is used to share to the rest of the network.
The downfalls are that this computer must be left on at all times because all the other computers rely on it for their Internet access, this computer must be equipped with 2 network connections (one to the Internet and one to the internal network) and ICS does not provide many features that come with using a router.
Connecting Multiple Computers to Broadband
Broadband, or high-speed, Internet connection is what many users currently use in their home. Along with high-speed Internet, many users may also use a router to allow multiple computers to connect to the Internet. This post will describe how a router is used to connect multiple computers. To make it easier to understand, I will use where you live as a comparison to how your computer is connected to the Internet.
What is an IP Address?
IP addresses are a series of numbers in the form: nnn.nnn.nnn.nnn, where nnn is a one to three digit number. An IP address is unique to an individual computer on a network, similar to how your home has a unique address. For an Internet connection, an IP address is supplied by your Internet Service Provider (ISP). In some cases, your ISP may provide you with more than one IP address, which allows you to connect multiple computers. As you will see later, however, you can still connect multiple computers with a single IP address.
Connecting a Single Computer
Connecting a single computer to your high-speed Internet is very simple to do. Simply connect a network cable into your modem, and then into the network card in your computer. Your computer will then be assigned an IP address from your ISP. For example, if your ISP assigned you the IP address of 24.24.50.17, then your computer will have that IP address. The figure below shows the connection.
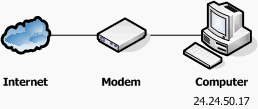
When you make a request to a server, such as for a Web page, the Web server knows which IP address made the request. The information is then sent through the Internet and back to your computer. This is similar to when someone sends you mail to your home. The address on the mail allows it to be delivered to your home and not somewhere else.
Connecting Multiple Computers
How can multiple computers connect if only one address is assigned? When you make a request for a Web page, how does it know which computer requested that page? Let’s take our home analogy one step further. Let’s say instead of living in a house, you live in an apartment. When someone sends you mail, they not only include your address but also an apartment number. This number is internal to your apartment building and every apartment has its own unique number. Similarly, multiple computers can connect to the Internet if they each had there own unique local IP address. This can be handled by a router.
A router is a piece of hardware that connects directly to the modem. Each computer is then connected to the router, instead of the modem. Now instead of your computer having the IP address supplied by your ISP, your router now is assigned that IP address. This is similar to your router acting as the apartment building.
The beauty of a router is that it can assign its own local IP addresses. When you connect a computer to the router it now receives one of the IP addresses assigned by your router, similar to how each apartment has it’s own number. Now when you make a request for a Web page, the request is sent using the same ISP address, but this time it is assigned to the router. When the Web page is returned, the router receives the request, and sends it locally to the computer that requested the page.
The router also has its own local address that is similar to the local IP addresses of the computers. So now the router has two addresses assigned to it: an external one provided by your ISP, and a local one provided by it. This allows the router to connect to both the Internet and the local network. The figure below shows how the router and computers are connected, and the IP address assignment.
Note: The 192.168.xxx.xxx address are special IP addresses reserved for Local Area Networks (LANs).
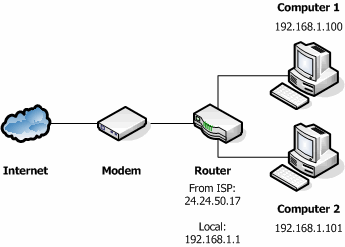
Managing a FTP or Web Server on Your Network
Let’s take a look at this scenario. You have a router connecting multiple computers to the Internet. But now you want to create a FTP or Web server. No problem. You setup the necessary software on a computer on your network, told someone outside your network the local IP address of your FTP server and they try to connect. They then discover that they can’t connect. Why? Its similar to someone mailing something to you by just specifying your apartment number and no address.
The IP address assigned to your computer is local to your network. You can connect to that computer from within your network, but not from the Internet. You will need to use your ISP-assigned IP address (the one assigned to your router) to have someone from the Internet connect to your FTP server. The problem is that your router is assigned that IP and not your computer, and since an IP address must be unique, how can two computers have the same IP? The answer: they can’t, but they don’t need to.
Routers have the ability to forward information on a port to a specific computer. A port is a numbered channel that data can be sent through on a network. You cannot physically see it as it is a virtual channel used extensively in networking for sending/receiving data. For FTP servers the default port is 21; however another port can be used.
Open your router setup and look for the port forwarding option. Specify the internal IP address of your FTP server and the port number and then save that information. Now when a user tries to access your FTP site, they must use the ISP IP address that is assigned to your router. The router will then notice that the data is being sent on port 21 and then forward it automatically to your FTP server. A Web server can be setup the same way, but its default port is usually 80. The figure below shows the router with the assigned IP address of 24.24.50.17, and the FTP server with the local address 192.168.1.101.
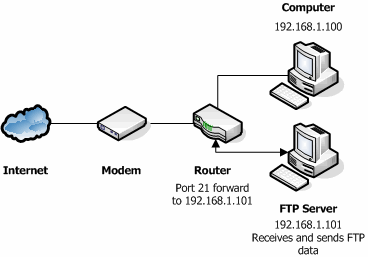
Note: By default a router will dynamically assign IP addresses to the computers connected to it. This means that the first computer to connect to the router will get the first available IP address, and the next will get the second, and so on. If you manage an FTP server, it may be easier to assign a static IP address to the computers to ensure that the FTP server always has the same IP address.
Summary
This post described how to connect one or more computers to one Internet connection. It is important to remember the following:
If you have one computer connected directly to the modem, then that computer will be assigned the IP address from your ISP.
When using a router, the the router will be assigned the IP address from your ISP. Any computers connected to the router will be assigned a local address by the router.
A router will have the ISP IP address and a local IP address. This allows it to connect to both the Internet and your network.
When setting up a computer as a FTP, Web, or other server to communicate over the Internet, it is important to use the router’s IP address to access your server. You will then need to forward the necessary port to your server.
What is an IP Address?
IP addresses are a series of numbers in the form: nnn.nnn.nnn.nnn, where nnn is a one to three digit number. An IP address is unique to an individual computer on a network, similar to how your home has a unique address. For an Internet connection, an IP address is supplied by your Internet Service Provider (ISP). In some cases, your ISP may provide you with more than one IP address, which allows you to connect multiple computers. As you will see later, however, you can still connect multiple computers with a single IP address.
Connecting a Single Computer
Connecting a single computer to your high-speed Internet is very simple to do. Simply connect a network cable into your modem, and then into the network card in your computer. Your computer will then be assigned an IP address from your ISP. For example, if your ISP assigned you the IP address of 24.24.50.17, then your computer will have that IP address. The figure below shows the connection.

When you make a request to a server, such as for a Web page, the Web server knows which IP address made the request. The information is then sent through the Internet and back to your computer. This is similar to when someone sends you mail to your home. The address on the mail allows it to be delivered to your home and not somewhere else.
Connecting Multiple Computers
How can multiple computers connect if only one address is assigned? When you make a request for a Web page, how does it know which computer requested that page? Let’s take our home analogy one step further. Let’s say instead of living in a house, you live in an apartment. When someone sends you mail, they not only include your address but also an apartment number. This number is internal to your apartment building and every apartment has its own unique number. Similarly, multiple computers can connect to the Internet if they each had there own unique local IP address. This can be handled by a router.
A router is a piece of hardware that connects directly to the modem. Each computer is then connected to the router, instead of the modem. Now instead of your computer having the IP address supplied by your ISP, your router now is assigned that IP address. This is similar to your router acting as the apartment building.
The beauty of a router is that it can assign its own local IP addresses. When you connect a computer to the router it now receives one of the IP addresses assigned by your router, similar to how each apartment has it’s own number. Now when you make a request for a Web page, the request is sent using the same ISP address, but this time it is assigned to the router. When the Web page is returned, the router receives the request, and sends it locally to the computer that requested the page.
The router also has its own local address that is similar to the local IP addresses of the computers. So now the router has two addresses assigned to it: an external one provided by your ISP, and a local one provided by it. This allows the router to connect to both the Internet and the local network. The figure below shows how the router and computers are connected, and the IP address assignment.
Note: The 192.168.xxx.xxx address are special IP addresses reserved for Local Area Networks (LANs).

Managing a FTP or Web Server on Your Network
Let’s take a look at this scenario. You have a router connecting multiple computers to the Internet. But now you want to create a FTP or Web server. No problem. You setup the necessary software on a computer on your network, told someone outside your network the local IP address of your FTP server and they try to connect. They then discover that they can’t connect. Why? Its similar to someone mailing something to you by just specifying your apartment number and no address.
The IP address assigned to your computer is local to your network. You can connect to that computer from within your network, but not from the Internet. You will need to use your ISP-assigned IP address (the one assigned to your router) to have someone from the Internet connect to your FTP server. The problem is that your router is assigned that IP and not your computer, and since an IP address must be unique, how can two computers have the same IP? The answer: they can’t, but they don’t need to.
Routers have the ability to forward information on a port to a specific computer. A port is a numbered channel that data can be sent through on a network. You cannot physically see it as it is a virtual channel used extensively in networking for sending/receiving data. For FTP servers the default port is 21; however another port can be used.
Open your router setup and look for the port forwarding option. Specify the internal IP address of your FTP server and the port number and then save that information. Now when a user tries to access your FTP site, they must use the ISP IP address that is assigned to your router. The router will then notice that the data is being sent on port 21 and then forward it automatically to your FTP server. A Web server can be setup the same way, but its default port is usually 80. The figure below shows the router with the assigned IP address of 24.24.50.17, and the FTP server with the local address 192.168.1.101.

Note: By default a router will dynamically assign IP addresses to the computers connected to it. This means that the first computer to connect to the router will get the first available IP address, and the next will get the second, and so on. If you manage an FTP server, it may be easier to assign a static IP address to the computers to ensure that the FTP server always has the same IP address.
Summary
This post described how to connect one or more computers to one Internet connection. It is important to remember the following:
If you have one computer connected directly to the modem, then that computer will be assigned the IP address from your ISP.
When using a router, the the router will be assigned the IP address from your ISP. Any computers connected to the router will be assigned a local address by the router.
A router will have the ISP IP address and a local IP address. This allows it to connect to both the Internet and your network.
When setting up a computer as a FTP, Web, or other server to communicate over the Internet, it is important to use the router’s IP address to access your server. You will then need to forward the necessary port to your server.
Subscribe to:
Posts (Atom)
